 |
by Dan Goodin from Ars Technica - All content on (#3EDT)
Company backs away from earlier claim there was no merit to security concerns.
|
Story
Lenovo apologizes for pre-loaded insecure adware "Superfish"Similar News
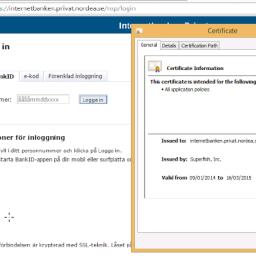 |
by Nate Anderson from Ars Technica - All content on (#3DVC)
It wasn't about the money!
|
