
Earlier this year the folks at PC-BSD announced they would be developing a new desktop environment by the name of Lumina. The official PC-BSD blog <
recently posted a progress update on the Lumina desktop that shows they are making huge progress. There are
screen shots and a list of updated features.
PC-BSD is a popular desktop-oriented BSD flavor that is really just FreeBSD with extras.
Lumina is a new light weight window manager built on Fluxbox using the Qt toolkit. The development is spearheaded by Ken Moore of the PC-BSD project.
There's lots more about Lumina
at their Lumina FAQ. Most important of all is the question "Why a new desktop environment?" Their answer is related to the fact that because the other desktops are built first on Linux they must be ported, which is taking more and more time and energy; furthermore, many desktops now depend on Linux-specific functionality that makes the port almost impossible.
The Lumina desktop will also provide BSD-specific features through its file manager, like full ZFS snapshot restore capability.
[Ed. note: sneak preview, but I was planning on doing this one for Distro Friday tomorrow. Stay tuned.]
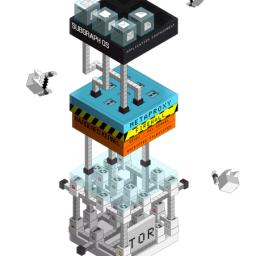
Tails was compromised, and everyone is wondering what is going to happen next. But a team of researchers in Canada hopes they have the answer:
Subgraph, an operating system resistant to zero-day exploits.
In Subgraph OS, any application a computer interacts with running the operating system is isolated in containers to prevent exploits from having a meaningful impact at the OS level. It uses the Grsecurity kernel, a patch applied to the Linux kernel that enhances security by limiting what processes can do. For example, with most operating systems, receiving an infected PDF making use of a zero-day vulnerability means before you realize it, there's malicious code running on your computer. ... he new OS is also, obviously, designed for complete anonymity. All the connections in the OS are intercepted by a metaproxy that then routes them through Tor. The metaproxy has some nifty tricks, too: it opens different Tor circuits for different apps, to avoid an attacker correlating traffic to the same origin.
Subgraph is based on Debian, PGP, and other open source technologies and products.

If you're tired of iOS, bored with Android, disgusted with Blackberry, and put off by Winphones, the folks over at Jolla would like to have a word with you.
Their Jolla phone, running a cutting-edge version of their Sailfish OS has just launched.If you hadn't heard, Jolla was founded by a bunch of ex-Nokia employees who decided to go solo with a Linux-based phone operating system when Nokia chose Elop and a Microsoft strategy. Will it work?
Having gone on retail sale at the end of 2013, it's been a busy and productive year for a company with an employee count that is in the low hundreds. Compare that to Microsoft, Apple, or Samsung, and you can put the success of the Jolla hardware and software into perspective. ...
The Jolla handset does not follow the normal paradigms for a smartphone user interface. As the smartphone moves away from the hackers and early supporters, improving the consumer experience has been one goal. The Sailfish UI is fast and flexible, and well-suited to one-handed usage. But it does take some getting used to. Jolla has improved the UI tutorial, and also added in dynamic hints and tips if the OS feels the user is 'stuck' looking for something in the UI.
The thing looks nice enough, but it's going to have to be slicker and sleeker than the existing alternatives to take traction. That said, there's no reason the market can be disrupted. Every time some pundit declares a winner, history proves them wrong.
 Prefer Windows 7 to Windows 8
Prefer Windows 7 to Windows 8? Too bad: you're not far away from not having the choice, for some editions. Some wholesalers are already reporting they will no longer be getting Windows 7 Home Premium or Windows 7 Ultimate after October:
Windows 7 Home Premium and Windows 7 Ultimate will be EOL on 10/31/14. Please note: This is ONLY Windows 7 Home Premium and Ultimate editions -- NOT Windows 7 Professional. Windows 7 Professional will still be around for the foreseeable future... No EOL date has been issued on Pro as of yet.
If you have customers that will require Windows 7 Home Premium beyond 10/31/14, please plan ahead. We may purchase Windows 7 Home Premium & Ultimate up until 10/31/14, but once that date has passed, Microsoft will no longer sell the item. At that point - what we have left in-stock is final! Please also remember that downgrading from Windows 8 Core to Windows 7 Home on system builds will no longer be an option after this date, either.
Extended support for Win7 is available until
January, 2020. But given how hard it's been to get people to move to Win8, you can only imagine Microsoft is looking forward to pulling the plug on 7 Pro as well.
Twenty years ago a guy by the name of
Jordan Hubbard began the first FreeBSD ports tree. Two decades later it's an essential part of any FreeBSD install, allowing source code-level access to a huge ecosystem of software, all installable in either binary package or make-config-install format. That's not Jordan's only contribution either: FreeBSD owes sysinstall and the original package management system to him as well (retired in FreeBSD 10.0-RELEASE for a next generation system).
In commemoration of the big 2-0,
BSDFrance commissioned this video. It's quite well done.
BSD/Linux users, what are your opinions of the ports tree vs. repositories vs. app stores? Happy 20th, FreeBSD Ports Tree.
[Ed. note: 2014-08-27 21:18 thrilled to see we now have our very own BSD topic. About time; there have been several BSD articles here!]
Well, unless you were holed up with Dick Cheney in the underground security bunker, you probably noticed Pipedot flipped the switch on a new feature that feeds articles from other sites. The idea is, as I understand it, anyone running Pipecode can eventually have a whole series of these feeds, and automatically populate their site with articles.
That led to a rash of new articles here, all of the Soylent comments, and a bit of anger over at Soylent despite NCommander having generously and magnanimously offered the feed of articles to Pipedot.
Nonetheless, this mirthful article suggestion poked up in the Pipe today:
Pipedot caught willfully plagiarizing Soylent News! As noted on https://soylentnews.org/comments.pl?sid=3587&cid=85807 and https://pipedot.org/story/2014-08-26/database-to-track-suspicious-memes-on-twitter and in particular, https://pipedot.org/comment/1409062920_n1_soylent_news_org , the majority of content being posted on pipedot.org is taken without permission from soylentnews.org
Given that the copyright of comments on soylentnews.org is not transferred from the people that posted them, this ongoing action constitutes wilful, mass copyright infringement.
You are hereby given notice on behalf of John Doe and Jane Doe * 4,000 under the US Digital Millennium Copyright Act 1998, as amended, Section 512(c)(3)(A) that:- ...
Glad nerds haven't lost their sense of humor. So, what did you think of the feature? Your comments here about the feed, the pipe, and the future direction of Pipedot.
There's an awful lot of sites out there offering you the latest in science, technology, gadgets, distros, and more. It's impossible to list them all here, but here's a representative sample of the big guns (plus Usenet!). Tick off any that you visit on a somewhat regular basis, and list others that you enjoy. This will help the editors and submitters better monitor those sites for interesting stories worth posting and discussing here.
The poll is here.
tdk (of
s'qute) has
announced a project that he has been working on the last couple of months that is of interest to those still using Windows.
DoxBox: Open-Source disk encryption for Windows. Think Truecrypt++
Features:
- Easy to use, with a 'wizard' for creating new 'DoxBoxes'.
- Full transparent encryption, DoxBoxes appear as removable disks in Windows Explorer.
- Explorer mode lets you access DoxBoxes when you don't have admin permissions.
- Compatible with Linux encryption, Cryptoloop "losetup", dm-crypt, and LUKS. Linux shell scripts support deniable encryption on Linux.
- Supports smartcards and security tokens.
- Encrypted DoxBoxes can be a file, a partition, or a whole disk.
- Opens legacy volumes created with FreeOTFE
- Runs on Windows Vista onwards (see note below for 64 bit versions).
- Supports numerous hash (including SHA-512, RIPEMD-320, Tiger) and encryption algorithms (Including AES, Twofish, and Serpent) in several modes (CBC, LRW, and XTS), giving more options than any other disk encryption software.
- Optional 'key files' let you use a thumb-drive as a key.
- Portable mode doesn't need to be installed and leaves little trace on 3rd party PCs (administrator rights needed).
- Deniable encryption protects you from 'rubber hose cryptography'.
GitHub Page,
Download Page
"Spooks have called upon the good people of Blighty to help protect an airline from attack by a vicious group of nerdy cyber-terrorists. That might sound like the secret services are getting a bit desperate, but don't worry kids: it's only a game.
The bods at GCHQ have announced a new part of the Cyber Security Challenge UK designed to unearth potential digital knights of the realm.
If you think you've got the stuff, and haven't read "Enders Game" so that the irony would interfere with your sense of patriotism,
have a look! Earlier this year the folks at PC-BSD announced they would be developing a new desktop environment by the name of Lumina. The official PC-BSD blog <recently posted a progress update on the Lumina desktop that shows they are making huge progress. There are screen shots and a list of updated features.
Earlier this year the folks at PC-BSD announced they would be developing a new desktop environment by the name of Lumina. The official PC-BSD blog <recently posted a progress update on the Lumina desktop that shows they are making huge progress. There are screen shots and a list of updated features.

