 |
by Remy Porter on (#60NZ9)
"We have an internal website that shows, among other things, the daily availability of my coworkers for the next three months to help with scheduling, especially when planning vacations," writes Alexander."This vacation planner data is represented as a table. An image of a table to be more precise."Displaying data as images is already a WTF. It's certainly not user friendly, it's definitely not accessible, and it makes one wonder whyyyy. That, however, is the least of the WTFs Alexander has in store for us.First, the front-end sent its HTTP requests to a single end-point. Every request went to the same URL. When the user clicked the button to show the vacation planner, the browser would submit a form- yes a form, creating a body which looked like:
|
 The Daily WTF
The Daily WTF
| Link | http://thedailywtf.com/ |
| Feed | http://syndication.thedailywtf.com/TheDailyWtf |
| Updated | 2026-02-17 17:17 |
 |
by Remy Porter on (#60MMH)
Madeline inherited some Python 2.7 code, with an eye towards upgrading it to a more modern Python version. This code generates CSV files, and it's opted to do this by cramming everything into a 2D array in memory and then dumping the array out with some join operations, and that's the real WTF, because that's a guaranteed way to generate invalid CSV files. Like so many things, the CSV files are actually way more complicated than people think.But we're going to focus in on a smaller subset of this pile of WTFs. I'll lead with the caveat from Madeline: "I've changed some of the variable names around, for a bit of anonymity, but couldn't get variable names quite as terrible as the original ones."
|
 |
by Remy Porter on (#60K8M)
Christopher Walker continues to struggle against ancient PHP applications in the automotive industry. With the point system behind him, there was a whole pile of internal applications for handling information about laws, misconceptions about the law, and other driver services.One, a home-grown CMS, was useful for publishing blog-style content about changes in the law. There was just one problem: if a post was published without a thumbnail, attempts to view that post failed with an error. It wasn't hard to find the offending line.
|
 |
by Remy Porter on (#60J42)
There's an old saying in programming: you don't have to spell correctly, you only have to spell consistently. As long as you mispell everything the same way, your language will understand your code. However, most editors and IDEs have spell-check integration, though, because it's hard to get everyone on a team to spell things wrong consistently.Unless, of course, you know just implement some bonus methods, like John's co-worker. This was frequently spammed in the Java codebase:
|
 |
by Remy Porter on (#60FD0)
|
 |
by Remy Porter on (#60DZN)
|
 |
by Alex Papadimoulis on (#60CM5)
|
 |
by Alex Papadimoulis on (#60B8N)
|
 |
by Mark Bowytz on (#609YB)
|
 |
by Lyle Seaman on (#60713)
I remember when gasoline was under a dollar a gallon inthe US! And penny candy was only a penny! And a poundsterling could buy you a decent dinner, not just a fewounces of meat product! And the euro! Let me tell you about the euro!!
|
 |
by Remy Porter on (#605MT)
Crystal Reports falls into that category of tool which promises to help end users accomplish technical tasks easily. They can point it at a database, ask the database a question, and voila, a report pops out, complete with pretty fonts and colors.Like any such tool, however, there's a point where it starts getting technical. Jon's company passed that point ages ago, and hired on a dedicated Crystal Reports Developer to write reports that were too complicated for the end users. But even that has its limits, and eventually, their reporting needs outgrew what a Crystal Report implemented by their dedicated developer could do.So Jon's team was handed a pile of reports and told, "implement these as stored procedures in SqlServer." Now, there wasn't anything so fancy as being given requirements or any sort of description about what the reports were for, or what they did, or what would qualify as a successful port version an error. The reports themselves were the requirements: reverse engineer them exactly as written, doing a 1-to-1 mapping wherever possible.That was mostly fine, but there were a few "special" points in the original reports, where the developer had implemented their own custom Crystal Report functions. Including their own custom date functions. Like this one:
|
 |
by Remy Porter on (#6045Y)
Another day, another time where someone from Brian's team needs to log into their MySQL database and kill a query. This particular query hangs while holding a lock, which hangs up every other query which needs to touch this table, which is a lot of them.
|
 |
by Remy Porter on (#602SR)
Taffer is the team lead on a team making security products. As such, they have very strict policies about how they write their code, they have very thorough code review systems, and they also have automated tests for everything.And yet, things can still slip through.Taffer submitted this change. It passed two code reviews. It didn't cause any unit tests to fail. It made it into the main branch, and sat there for two months. A team of very experienced, very senior developers didn't catch this glitch until a new hire happened to notice it during a review for something else.
|
 |
by Remy Porter on (#601HA)
Annalise has a pile of… unfortunate JavaScript. It's thousands of files with no real organization or logic behind their organization. It's got so much tech debt that it takes a full time developer just to keep it running, let alone provide support or add features or fix bugs. And the backlog of features and bugs is so long that it's best described in terms of א.Which is to say, there's a lot in there that nobody understands. So when you see a bunch of callbacks registered to onFunctionCall, you might assume that this handler is doing… something. You'd be wrong.
|
 |
by Lyle Seaman on (#5ZYWV)
Yankee Ezra A.explains the screenshot below at some length. Says he:"I live in Newton, MA, an affluent, wealthy suburb of Boston.In general, city services are excellent, although thehome page of the website is a bit crowded, so I was gladto get an email with a link to the page where I couldsee how the city is handling my request/complaint aboutsidewalks, via the city's 311 service (I have no ideawhat the 311 stands for)When I went to the website, I found what you see in thephoto.I guess one can't really complain about one small errorin a large website." It's certainly an effective strategyfor keeping the complaints box empty!
|
 |
by Remy Porter on (#5ZXGT)
Guillaume's company frequently uses consultants. It's a pretty standard setup: Guillaume's employer has many multi-year projects in flight, all of which are layered atop an existing ecosystem of in-house "do everything" applications, each full of their own WTFs.Because of the complexity, Guillaume's team has a pretty strict code review policy. Someone new to the team will write a merge request, a senior developer will coldly review it and provide huge amounts of comments. By the end of the process, the senior team member may have provided most of the code and architecture via those code review comments, and the junior member is left to just follow the instructions.When Guillaume was tasked to review a senior contractor's submission though, that felt like a change of pace. Guillaume still left a lot of comments, but it was more obviously a good merge request. Still, "good" is not "ready for production", and Guillaume ended up in a conflict with management: they wanted the merge now, he wanted the merge right: in compliance with their standards, containing no obvious gotchas, and with clear comments and documentation."This is a senior consultant," Guillaume's boss said, "and they know the product. You need to have a little trust in your senior developers' skills."Guillaume tried to explain that it wasn't about trust; everyone needed their code reviewed because more eyes was better. That didn't budge management, so Guillaume found a compromise: the merge could happen, if there was a follow up to fix the "less urgent comments". That made the users happy, that made Guillaume- well, if not happy, not irritated, and it definitely made the boss happy.One of those "less urgent" comments was on this line:
|
 |
by Remy Porter on (#5ZW4H)
Managing true and false values is historically challenging. In the world of C, there's even a history to those challenges. Prior to the C99 standard, there wasn't a standardized version of boolean values, but there was a convention which most applications followed, based on how C conditionals and boolean logic works.In C, anything non-zero is considered "true". So, if(0) { … } won't execute the branch, but if(99) { … } will. As a result, when people wanted to make boolean equivalents, they'd use the C preprocessors to specify something like:
|
 |
by Remy Porter on (#5ZTSB)
Matt P was spending a few hours trawling through a Java code base, working through the poorly documented logic and the bugs and the odd conventions. It was the kind of code base that rightly eschewed "magic numbers", favoring constants, but was also the kind of code base which took that to an extreme which arguably didn't help readability.For example:
|
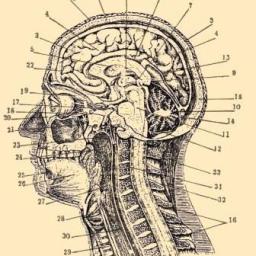 |
by snoofle on (#5ZSQQ)
|
 |
by Lyle Seaman on (#5ZPYQ)
This week brings an ongoing installment in a long-running gag, and a plea for helpwith a truly execrable pun. Can someone please find me some map-related material in Idaho? I promise not to credit you directly!Workaholic Stuart Longland flexes "Yes, I'm working on a Sunday. And yes, I've workedsome long hours in the past. But 56 hours in one day?I don't know whether to crow or cry!ButTRWTF is the fact these phantom work entriesre-incarnate after I delete them." In his own defense, Stuart explains (and I concur)"Monday-Friday is fairly meaningless after COVID and the Queensland Floods."
|
 |
by Remy Porter on (#5ZNMC)
In many places, driver's licenses work on a point system. As you commit infractions, you gain or lose points, when your point score hits a certain threshold, your insurance company raises your rates or you may even lose your driver's license. Where Christopher Walker lives, you start with twelve points, and each infraction takes a few away. Once a year, you have the option to attend a workshop on safe driving, where you can then regain a few of those points.It's complicated and tedious, so several organizations, from the local department of motor vehicles to various insurance companies, have set up systems to manage this information. One of those organizations built a PHP application about fifteen years ago, and it gradually grew in kruft and complexity and confusion from that point forward. It works, but it's entirely unmaintainable.So Christopher was hired to help upgrade it to something hopefully supportable. It's still in PHP, but it's redesigned to use some best practices, switch to Laravel as its framework, and basically be as modular and component-oriented as possible.The real challenge was porting the existing data into the new system. The old schema was a mess. The "simple" problems were all around the fact that once upon a time the database only used ASCII, but was eventually upgraded to use UTF-8, but however that was done made it so that many characters like 'é' got mangled into '‡' or '§'.But all of that was nothing compared to the problems updating the revision history tables. The other developers had given up on the revision/audit history many years ago. Instead of providing detailed reports, they simply displayed "[username] changed this participant."The application tracked an audit log, and it was fairly thorough. At first glance, it even seemed pretty sensible. It had a timestamp, an action code (like "USRUPDATE" or "USRCREATE"), a "detailsaction" which contained what appeared to contain the new value of a modified field, and then a "request" which just seemed to log the raw SQL run to alter the table. That last one didn't seem important, so Christopher went ahead and started porting the old table to the new database.That's when Christopher hit the first speed bump. Some of the records were sane, comprehensible audit logs. Some of them simply weren't. For some of them, the audit fields conveyed no information. For others, you needed to look at the request field and try and reconstruct what happened from the raw SQL. Except that was easier said than done: many of the queries in the audit log referenced tables and fields which no longer existed, or had been renamed at some point. By combing through the huge pile of data, Christopher was able to determine that there were only about 20 different ways those queries got deprecated, so it wasn't too hard to come up with a script that could translate them into the new architecture.The other unusual edge case were that instead of storing SQL in the field, many stored a condensed array representing the row that was altered, like:a:23:{s:14:"participantsid";i:123456;s:5:"titre";s:8:"Monsieur";s:3:"nom";s:5:"[LAST_NAME]";s:6:"nom_jf";s:0:"";s:6:"prenom";s:6:"[FIRST_NAME]";s:10:"profession";s:1:"0";s:14:"naissance_date";s:10:"xxxx-xx-xx";s:14:"naissance_lieu";s:15:"STRASBOURG (67)";s:8:"adresse1";s:20:"[REDACTED]";s:8:"adresse2";s:0:"";s:11:"code_postal";s:5:"12345";s:5:"ville";s:9:"[REDACTED]";s:4:"tel1";s:14:"[REDACTED]";s:4:"tel2";s:0:"";s:5:"email";s:24:"[REDACTED]@gmail.com";s:6:"membre";s:0:"";s:15:"immatriculation";s:0:"";s:2:"ac";s:3:"NON";s:12:"permisnumero";s:12:"[REDACTED]";s:10:"permisdate";s:10:"2019-01-21";s:10:"permislieu";s:9:"PREFET 67";s:8:"remarque";s:0:"";s:14:"naissance_pays";s:0:"";}That wasn't terrible to manage, aside from the fact that the dumps didn't actually reference existing tables and fields. Christopher could figure out what the replacement tables and fields were and map the data back to actual audit log entries.That got Christopher 90% of the way there. But 90% isn't all the way, and the last ten percent was going to take a lot more time. Or perhaps was going to be impossible to do. Because the remaining audit log records stored queries that had nothing to do with the entity that was changed. Many of them weren't even modification statements.For example, the audit log entry that seemed to be about updating a workshop's status from "active" to "cancelled" was purportedly done by this query: SELECT lieux.departement FROM lieux JOIN stages ON stages.lieuxid = lieux.lieuxid WHERE stages.types = 'PAP' AND stages.stagesid ='123456'.Christopher summarizes:
|
 |
by Remy Porter on (#5ZMAN)
Linda discovered a new anti-pattern, helpfully explained with comments.
|
 |
by Remy Porter on (#5ZJW3)
Kerin inherited a scheduling application for a university. This application stored the scheduled days for a class in the database… as one comma-separated field. This was a problem for Kerin, who was hired to add predictive scheduling and classroom density measurements to the system.This particular function was written to take that data and transform it for display. Sort of.
|
 |
by Remy Porter on (#5ZHHS)
Nullable types, at least in theory, make our code simpler and easier to maintain. If nothing else, we know when there's a risk of a null value, and can handle it with some grace. At least, that's how it works if we understand what they do.Boaz's co-worker knows that nullables are valuable, but doesn't quite get it.
|
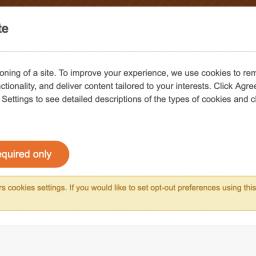 |
by Lyle Seaman on (#5ZETN)
Danish cookie connoisseur Jørgen N. contributes our starter course this week. "Cloudera has an interesting way of implementing "Required only" cookies." It's an exercise for the frist poster to explain to the peanut gallerywhat's so distasteful about third-party cookies.
|
 |
by Remy Porter on (#5ZDE5)
"Don't concatenate long strings," is generally solid advice in most languages. Due to internal representations, strings are frequently immutable and of a fixed length, so a block like this:
|
 |
by Remy Porter on (#5ZC3Z)
Martin's company had written a set of command line tools which their internal analysts could then string together via shell scripts to do their work. It was finicky and fragile, but frankly didn't work too badly for most cases.There was one tool, however, which seemed to be the source of an unfair number of problems. Eventually, Martin sat down with an analyst to see what was going wrong. The program would exit successfully, but wouldn't actually do any of the work it was supposed to. Instead of doing the normal thing and writing errors to STDERR, the tool wrote to a file. Which file, however, was determined by reading some shell variables, but the shell variables used by each of the tools were slightly different, because why would you build a consistent interface for your suite of analytical tools?Eventually, Martin was able to figure out where the errors were going, and saw that it was failing to connect to the backend database. That was a simple matter- just fix the connection string- but why was it exiting successfully when it couldn't connect?
|
 |
by Remy Porter on (#5ZARA)
Let's say you saw a method called StrToGuid, in a C# codebase. Your first thought might be: "Wait, isn't there a built in parse? Well, I guess maybe they might do some sort of exception handling. But it still doesn't seem right." And then you'd take a look at the method signature and see that it takes both a string, and an integer named counter, and you'd think: "Wait, what?"Henrik H had a similar experience. His team hired a new developer, someone with 15+ years of experience. This is what they contributed to the codebase:
|
 |
by Remy Porter on (#5Z9BM)
"There are a few more functions like this in the same file," writes Jenny, about today's submission. This is one which largely does speak for itself.
|
 |
by Lyle Seaman on (#5Z6MQ)
This week's edition of Err'd gets off to a flyingstart with one that came in "over the transom" as t'were.Ordinarily, expired certs are a bit mundane for thiscolumn, but in this case, where this foiblefetched up is at least worth a chuckle.Jim M. wrote directly to the editor with this explanation."If you're looking for compliance reports to prove that your cloudprovider has solid security practices, be wary of this WTF with Azure.Quoting the site, SOC 2 Type 2 attestation report addressesthe requirements set forth in the Cloud Security Alliance (CSA)Cloud Controls Matrix (CCM), and the Cloud Computing ComplianceCriteria Catalogue (C5:2020) created by the German FederalOffice for Information Security (BSI).Sounds impressive!The link for Azure DevOps SOC 2 Type 2 attestation reportgoes to this link,https://docs.microsoft.com/en-us/compliance/regulatory/offering-soc-2,which shows that the cert for this page has expired. Try it here:https://servicetrust.microsoft.com/ViewPage/MSComplianceGuideV3"
|
 |
by Remy Porter on (#5Z571)
Austin's team received a bug report. When their C# application tried to load certain settings, it would crash. Now, since this was a pretty severe issue in their production software, impacting a fair number of customers, everyone on the team dove in.It didn't take Austin long to spot the underlying problem, which isn't quite the WTF.
|
 |
by Remy Porter on (#5Z3R2)
In the endless quest to get asynchronous operations right, we're constantly changing approaches. From callbacks, to promises, to awaits, to observables. Observables are pretty straight forward: we observe something, like a socket or a HTTP request, and when something happens, we trigger some callbacks. In a lightly pseudocode version, it might look something like:
|
 |
by Remy Porter on (#5Z2B4)
Lacy's co-worker needed to collect groups of strings into "clusters"- literally arrays of arrays of strings. Of great importance was knowing how many groups were in each cluster.Making this more complicated, there was an array list of clusters. Obviously, there's a code smell just in this data organization- ArrayList<ArrayList<String[]>> is not a healthy sounding type name. There's probably a better way to express that.That said, the data structure is pretty easy to understand: I have an outer ArrayList. Each item in the ArrayList is another ArrayList (called a cluster), and each one of those contains an array of strings (called an answer, in their application domain).So, here's the question: for a set of clusters, what is the largest number of answers contained in any single cluster?There's an obvious solution to this- it's a pretty basic max problem. There's an obviously wrong solution. Guess which one Lacy found in the codebase?
|
 |
by Remy Porter on (#5Z108)
Giles's company has a hard time with doing things in the database.In today's example, they attempt the very challenging task of generating unique IDs in a SQL Server database. Now, what you're about to see follows the basic pattern of "generate a random number and see if it's already been used", which is a fairly common anti-pattern, but it's managed to do this in some of the worst ways I've ever seen. And it can't even hide behind the defense of being written a long time ago- it's a handful of years old.Comments to this C# code have been added by Giles, and no, there were no comments.
|
 |
by Remy Porter on (#5YX38)
Carolyn's company has a bunch of stringly-typed enums. That's already a problem, even in Python, but the other problem is that they need to display these in a human readable format. So, "ProductCategory" needs to become "Product Category". Now, it's true that every one of these stringly typed enums follows the PascalCase convention. It's also true that the list of them is constantly growing.So this is the method someone wrote for formatting:
|
 |
by Remy Porter on (#5YVWD)
Steve's predecessor knows: sometimes, stuff happens that makes you go "WTF". While Steve was reviewing some inherited PHP code, he discovered that this predecessor had built some code to handle those situations.
|
 |
by Remy Porter on (#5YTFA)
When companies reinvent their own accounting software, they usually start from the (reasonable) position of just mirroring basic accounting processes. You have transactions, for an amount, and then tagged with information about what the transaction actually represents. So, for example, if you wanted to find all the transactions which represent tax paid, you'd need to filter on some metadata and then sum up the amounts.It quickly gets more complicated. In some organizations, that complexity keeps growing, as it turns out that each department uses slightly different codes, the rules change over time, this central accounting database gradually eats older databases which had wildly different rules. Before long, you end up with a database so krufty that it's a miracle SQL Server doesn't just up and quit.That's the situation Giles W found himself in. What follows is an example query, which exists to answer the simple question: on 20th December, 2013, how much tax was paid across all transactions? For most database designs, that might be an expensive query, but hopefully a simple query. For this one… well… they may need to do some redesigning. Note the horizontal scrolling on today's code, there was no good place for me to add linebreaks for readability.
|
 |
by Remy Porter on (#5YS6R)
Shery sends us perfectly innocent looking Java class, marked up with some annotations. The goal of this class is to have an object which contains a list of names that is definitely not null. Let's see how we did.
|
 |
by Lyle Seaman on (#5YPEK)
Shocked sharerRob J. blurts "I feel like that voltage is a tad high."
|
 |
by Remy Porter on (#5YN13)
If you're working in a research field, references matter- specifically, the citations made by your paper and the citations eventually made against yours. But when programming, references can be hard.
|
 |
by Remy Porter on (#5YKP6)
It's not nothing to never write confusing English. And it doesn't never influence the code that we write. Don't fail to look at this anti-pattern from today's un-named submitter.
|
 |
by Remy Porter on (#5YJ9R)
In addition to being a developer, Beatrix W manages a few small email servers, which means she sometimes needs to evaluate the kinds of messages arriving and their origins, especially when they're suspicious. One such suspicious message arrived, complete with a few malicious links, and some hints of possibly being the start of a spear-phishing attack.That was concerning, and as it turns out, the email came through a vendor who specializes in sending marketing emails- but the requested sort (or at least the sort where you got confused about which box to uncheck at checkout and accidentially signed yourself up for a newsletter). So Beatrix tracked down the contact form on the company website.She filled out the form with a description of the issue. The form had a handy-dandy "Attachments" field, and the instructions said, "Attach the suspicious email with its full email headers." So, she copy/pasted the suspicious email, headers included, into a text file, and attached the text file. She reviewed her work, confirmed that the attachment had uploaded successfully, and then pushed "Send". A copy of her submission arrived in her inbox, attachment and all, so she filed it away and forgot about it.Two weeks later, the vendor replied.
|
 |
by Remy Porter on (#5YH13)
While JavaScript (and TypeScript) may have conquered the world, those languages have… unusual conventions relative to some lower level languages you might encounter. I recently was having a debate with a C-guru, who lamented all the abstractions and promised that well written C-code would forever be faster, more compact, and easier to read that the equivalent code in a higher level language.That may or may not be true (it's not), but I understand his point of view.Lily comes from a background where she's used to writing lower level code, mostly C or C++ style languages. So when she tried to adapt to typescript, the idea that everything was a reference was inconvenient. An example of a thing which flummoxed her:
|
 |
by Lyle Seaman on (#5YEEB)
While we don't know the precise taxonomy of the fabled dilemma, this week's submissions include a few wild examples.Jon has captured a classic sample of the anticancelling cancel, reporting"While bulk-deleting files from an S3 bucket, Amazondangled a carrot in front of me only to cruelly whip itaway at the last moment."
|
 |
by Jane Bailey on (#5YD29)
Sandra from Initrovent, previously featured here on the site, has finally left that job, finding herself at InitAg instead. InitAg is a small agricultural tech startup, a little rough around the edges for a data science company, but overall functional. With one notable exception: The customer portal.The customer portal is a mid-sized Symfony application, built up over the course of 5 years by an externally contracted one-man shop (let's call him Bjørn) who jealously guarded the source code up until the point he decided to drop InitAg as a client in late 2021. Upon informing them he was dropping them, he took a few weeks to clean up some of the code before giving it to InitAg. The Symfony part was mostly all right, with a few small WTFs but nothing too surprising. However, part of the portal's task was the slicing of large (>1GB) image files into smaller chunks for display in a browser, and a few other time-intensive tasks. Which brings us to today's topic: queuing.There's lots of ways to do queuing right. If you're working in the modern day, you're probably going to use RabbitMQ or another AMQP message broker. If it's 1995, probably the Linux system queue. But Bjørn was a fan of "keeping things simple". What mechanism did he choose for the queue? A collection of "task files" (with no defined structure) in a shared directory, and a bash script on an every-5-minutes cron job polling that directory for the next task, which would then trigger other bash scripts that actually performed the long-running operation. Some of these scripts were many hundreds of lines long, and without any form of documentation or comments to explain why they were shuffling files around or performing other operations.Of course, that's not all. It turns out that a large number of the scripts were unused (tasks that had been superseded or were no longer needed), but only Bjørn knew which ones were and weren't active.Bjørn's reasoning for all of this? "I like to keep things simple."It also didn't help that Bjørn had terrible git hygiene and seemingly didn't know about .gitignore, so the directory with all these scripts in it contained about 7,000 of these task files.Thankfully, this WTF has a happy ending: Sandra was eventually able to kill off the home-built queuing mechanism and the vast majority of the scripts, and replace the whole mess with a nice RabbitMQ consumer. Still, you gotta love the guys who like to "keep things simple" by avoiding proven, robust solutions in favor of homebrew nonsense. [Advertisement] BuildMaster allows you to create a self-service release management platform that allows different teams to manage their applications. Explore how!
|
 |
by Remy Porter on (#5YBSB)
Initech sold some expensive devices which supported location tracking. Their customers wanted to track the location of these devices, with full history of all previous locations, down to five minute increments.When Eurydice F joined the team, she understood that it would be a lot of data to manage. She was an experienced DBA, and had all sorts of ideas about how you might partition the database to make that scale of data manageable, and the ways you would index it to make access and retrieval efficient.What she found instead was a table called DEVICELOGDAY. It had three fields. The first was a date- only a date, no time information, the second was an integer field simply called deviceId, and the third was a CLOB field called data.There was also a temporary table, a transaction-local table, simply called DEVICELOG. This had more reasonable fields- a timestamp, a device ID, a lat/lon pair.The secret of the dataflow existed in two stored procedures, PACKLOGDAY and UNPACKLOGDAY. A previous developer had seen "we need to store a row for every device, every five minutes" as an unbearable transaction burden. So instead, they decided to store one row per device, per day. That was DEVICELOGDAY. Every five minutes, a device would report its location and put that location in the DEVICELOG temporary table. Then PACKLOGDAY would be called, with the device ID as a parameter.PACKLOGDAY would take all rows in DEVICELOG with that device ID (which, as its a transaction-local temp table, would be the only rows in that table), and append them to the data column in DEVICELOGDAY for that device and that day, as a character-separated-values entry, e.g.:
|
 |
by Ellis Morning on (#5YAGM)
In 1981, Mark was hired at a company that produced minicomputers widely used in retail establishments and small/medium businesses. On the first day, Roger gave him a tour of the plant and introduced him to his new coworkers. After shaking hands and parting ways with Walt, the Manufacturing QA manager, Roger beckoned Mark to lean in close with an impish smirk."See, with each system we sell, we send out a response card that the installing CE or customer is supposed to fill out, telling us about any problems with the installation," Roger said. "One time, a 'squawk card' came back from a customer with the comment, Two dead rats in power supply. You know what Walt sent back? Must be shipping damage. They were alive when they left here."Mark laughed, but then also wondered if maybe he was being pranked as the FNG. "Did that really happen? If so, how is he still working here?""It did happen. Follow me!"Roger led him to the hallway just outside the cafeteria, over to a lit trophy case. He pointed inside at a plaque with an image of the squawk card mounted on it, response and all."There were some people who were pissed off, but, Walt's worked here for ages and has a ton of friends at Corporate," Roger explained. "He was fine! And he's a legend around here to this day."To Mark, it seemed a good omen for the kind of company and culture he'd signed onto. As the years passed, he got to tell the story to several new hires himself.Through multiple corporate spinoffs, mergers, and acquisitions, the plaque in the trophy case endured. It was still there when Mark finally parted ways with the company in 2009, and we can only hope that this corporate legend still endures. [Advertisement] Utilize BuildMaster to release your software with confidence, at the pace your business demands. Download today!
|
 |
by Jake Vinson on (#5Y9DP)
|
 |
by Lyle Seaman on (#5Y719)
During this, America's national season of shared trauma, ourregular contributor Mr. Bargle shares a bit of levity whichmay lighten your mood ever so slightly.Argle Bargle explains"My girlfriend is Thai. She speaks English, but not on anadvanced level, so when we chat, I typically translate toThai. I learned long ago to reverse the translation tomake sure the translation says what I meant. My girlfriendtook a leave of absence from her research position to bean entrepreneur. April 13-15 is the holiday of Songkran:Thailand's New Year celebration. She said she would toobusy to chat with me until the 15th. I mentioned that the15th is America's tax day. As a precaution, I translatedit and then reversed. The attached image is clearly notan error, but it's a helluva WTF. On the left is LOL...tax day in the USA in Thai. On the right is.... OMG."
|
 |
by Remy Porter on (#5Y5TG)
SQL injection attacks are, in most environments, easy to avoid. Pass user input through parameterized commands and never do any string munging to build your SQL queries. And yet, we constantly see places where people fail to do this correctly.Eric's co-worker is one of "those" people. They were aware of what SQL injection was, and why it was a risk, but instead of using PHP's built-in functionality for avoiding it, they reinvented the wheel- now in a triangular shape!
|