by Mark Bowytz on (#2YBP3)
"You know, usually these statements are just marketing B.S., but I think this guy's got the right idea," wrote Philip K.
| Link | http://thedailywtf.com/ |
| Feed | http://syndication.thedailywtf.com/TheDailyWtf |
| Updated | 2026-03-06 09:16 |
 |
by Remy Porter on (#2Y8D5)
About two years ago, we took a little trip to the Galapagos- a tiny, isolated island where processes and coding practices evolved… a bit differently. Calvin, as an invasive species, brought in new ways of doing things- like source control, automated builds, and continuous integration- and changed the landscape of the island forever.Or so it seemed, until the first hiccup. Shortly after putting all of the code into source control and automating the builds, the application started failing in production. Specifically, the web service calls out to a third party web service for a few operations, and those calls universally failed in production.“Now,†Hank, the previous developer and now Calvin’s supervisor, “I thought you said this should make our deployments more reliable. Now, we got all these extra servers, and it just plumb don’t work.â€â€œWe’re changing processes,†Calvin said, “so a glitch could happen easily. I’ll look into it.â€â€œLooking into it†was a bit more of a challenge than it should have been. The code was a pasta-golem: a gigantic monolith of spaghetti. It had no automated tests, and wasn’t structured in a way that made it easy to test. Logging was nonexistent.Still, Calvin’s changes to the organization helped. For starters, there was a brand new test server he could use to replicate the issue. He fired up his testing scripts, ran them against the test server, and… everything worked just fine.Calvin checked the build logs, to confirm that both test and production had the same version, and they did. So next, he pulled a copy of the code down to his machine, and ran it. Everything worked again. Twiddling the config files didn’t accomplish anything. He build a version of the service configured for remote debugging, and chucked it up to the production server… and the error went away. Everything suddenly started working fine.Quickly, he reverted production. On his local machine, he did something he’d never really had call to do- he flipped the build flag from “Debug†to “Release†and recompiled. The service hung. When built in “Release†mode, the resulting DLL had a bug that caused a hang, but it was something that never appeared when built in “Debug†mode.“I reckon you’re still workin’ on this,†Hank asked, as he ambled by Calvin’s office, thumbs hooked in his belt loops. “I’m sure you’ve got a smart solution, and I ain’t one to gloat, but this ain’t never happened the old way.â€â€œWell, I can get a temporary fix up into production,†Calvin said. He quickly threw a debug build up onto production, which wouldn’t have the bug. “But I have to hunt for the underlying cause.â€â€œI guess I just don’t see why we can’t build right on the shared folder, is all.â€â€œThis problem would have cropped up there,†Calvin said. “Once we build for Release, the problem crops up. It’s probably a preprocessor directive.â€â€œA what now?â€Hank’s ignorance about preprocessor directives was quickly confirmed by a search through the code- there was absolutely no #if statements in there. Calvin spent the next few hours staring at this block of code, which is where the application seemed to hang:
|
 |
by Remy Porter on (#2Y4YN)
Tim was debugging one of those multithreading bugs, where there appeared to be a race condition of some kind. The developer who had initially written the code denied that such a thing could exist: “It’s impossible, I used locks to synchronize the threads!â€Well, he did use locks at the very least.
|
 |
by Jane Bailey on (#2Y1M9)
There are many kinds of jackasses in this world, from the pretentious prick to the smug cynic. Each has their own flavor of awfulness, their own way of making you hate not only them but the entire world that gave birth to them. This story is about one kind of jackass in particular, perhaps the most classic flavor: the man so sure of his own greatness that he becomes enraged at the world whenever it fails to bow before his massive intellect.You see these people a lot on Twitter these days. With self-righteous fury, they demand that you get with the program and acknowledge their clear superiority. But as obnoxious as they are online, they're worse in person ... especially if they turn up at your job interview.Today's candidate applied for a job at a government IT department. Unlike stories you've seen on this site before, this government shop was actually fairly efficient and pleasant to work for. They were hiring Java developers, preferably ones that also had UI and database skills. As such, they had over 100 CVs to skim through for their first 2 positions. After removing those written in crayon, with massive coffee rings obscuring the text, or which had return addresses in prison, they were able to narrow the field to a mere 30, but it was still far more candidates than they wanted to interview in a few short days.But interview they did. At 10 candidates a day, they barely had time to weed through people; however, it didn't take long to eliminate most of the candidates. Some lacked a basic understanding of computers, such as how to launch applications when they're not strewn across the desktop. Others lacked a basic understanding of programming, being entirely unable to tell Java apart from Microsoft Word. Still others—disturbingly many others—lacked a basic understanding of hygiene.For Round 2, they decided only to work with agencies they'd had firsthand experience with, either from that office or from previous companies. They also put together a quick "sniff test" to filter the wheat from the chaff. This 30-minute test checked for basic logic skills, including some open-ended CS questions and Java code to debug. They were looking more for the explanations behind the answers than the answers themselves, hoping to get some idea of how these people reasoned.It worked like a charm. Those who scored under 50% were always appalling in the interview, and those who scored highly were always at worst acceptable. They quickly found their candidates. When it came time to fill the next junior opening, the decision was unanimous: they would use the sniff test as a screen, refusing to interview anyone who failed.Enter The Architect, our aforementioned jackass. This guy seemed pretty good on paper: "10 years experience in infrastructure architecture, design patterns, certifications, and software development practices" according to his cover letter. Applying for a junior role was a bit odd for this veteran, to be sure, but they gave him the test anyway.And boy, did he fail. His final score was a mere 5%. Every answer included a tirade about how the question was wrong. Every. Single. One.Some of you may not believe this man exists. But some of you have met him, or one of his many counterparts the world over. This is the man who, when faced with a question like:
|
 |
by Remy Porter on (#2XYCS)
Groovy was one of those programming languages that spent about six months as the trendy language du jour, and I haven’t heard much about it since. If I were to learn it, I’d want to learn by example- going through real-world Groovy code and seeing how it works.An anonymous submitter has provided one sample for me to learn from:
|
 |
 |
by Remy Porter on (#2XFWT)
About a decade ago, Gerald worked at a European nuclear plant. There was a “minor†issue where a controller connected to a high-voltage power supply would start missing out on status messages. “Minorâ€, because it didn’t really pose a risk to life and limb- but still, any malfunction with a controller attached to a high-voltage power supply in a nuclear power plant needs to be addressed.So Gerald went off and got the code. It was on a file share, in a file called final.zip. Or, wait, was it in the file called real-final.zip? Or installed.zip? Or, finalnew.zip?It took a few tries, but eventually he picked out the correct one. To his surprise, in addition to the .c and .h files he expected to see, there was also a mysterious .xls. And that’s where things went bad.Pause for a moment to consider a problem: you receive a byte containing an set of flags to represent an error code. So, you need to check each individual bit to understand what the exact error is. At this point, you’re probably reaching for a bitshift operator, because that’s the easiest way to do it.I want you to imagine, for a moment, however, that you don’t really know C, or bitwise operations, or even what a bit is. Instead, you know two things: that there are 255 possible error codes, and how to use Excel. With those gaps in knowledge, you might perhaps, just manually write an Excel spreadsheet with every possible option, using Excel's range-drag operation to fill in the columns with easily predictable values. You might do this for 254 rows of data. Which, as a note, the range of possible values is 255, so guess what was causing the error?
|
 |
by Jane Bailey on (#2XCDW)
She'd resisted the call for years. As a senior developer, Makoto knew how the story ended: one day, she'd be drafted into the ranks of the manager, forswearing her true love webdev. When her boss was sacked unexpectedly, mere weeks after the most senior dev quit, she looked around and realized she was holding the short straw. She was the most senior. This is her story.As she settled into her new responsibilities, Makoto started coming in earlier and earlier in the hopes of getting some development work done. As such, she started to get accustomed to the rhythm of the morning shift, before most devs had rolled out of bed, but after the night shift ops guys had gone home.Bad sign number 1: the CEO wandering past, looking a bit lost and vaguely concerned."Can I help you?" Makoto asked, putting down her breakfast pastry.Bad sign number 2 was his reply: "Does the Internet look down to you?"Makoto quickly pulled up her favorite Internet test site, /r/aww, to verify that she still had connectivity. "Seems all right to me.""Well, I can't get online."Webdev-Makoto would've shrugged and thought, Not my circus. Manager-Makoto forced a grin onto her face and said, "I'll get my guys on that.""Thanks, you're a real champ." Satisfied, the CEO wandered back to whatever it was he did all day, leaving Makoto to explain a problem she wasn't experiencing to guys way more qualified to work on this than she was.Hoping to explain the discrepancy, she unplugged her laptop. This time, the adorable kittens failed to load."Success!" she told the empty office. "This is officially some weird wi-fi problem."She drafted up a notice to that effect, sent it to the office mailing list, and assigned her teammate Sven to find and fix the problem. By 9:00 AM, all was well, and her team had sent out an update to that effect.Now well into her daily routine, Makoto put the incident behind her. After all, it was resolved, wasn't it?4:00 PM rolled around, and Makoto was somehow the recipient for an angry email from Greg in Sales. Is the internet still out? I need to close out my sales!!! Why hasn't your team fixed this yet! We could lose $300,000 if I can't close out my sales by 5PM!!!!!Makoto rolled her eyes at the unnecessary number of exclamation points and checked the sales pipeline. Sure enough, there was nothing preventing her from accessing Greg's queue and verifying that all $100 worth of sales were present and accounted for.Makoto cracked her knuckles and crafted the most polite response she could muster: As per my update at 9am, the Internet is back online and you should be able to perform any and all job duties at this time.The reply came 2 minutes later: I cannot close my opportunities!!!Makoto forwarded the email chain to Sven before rolling over to his desk. "Greg's being a drama llama again. Can you pull the firewall logs and prove he's got Internet?""'Course."10 minutes and 4 raised eyebrows later, Sven replied to the ticket, copying Greg's boss and attaching a screenshot of the logs. As Makoto stated, we are online at this time. Is it possible your computer received a virus from browsing PornHub since 9:30 this morning?Greg spent the next day in meetings with HR, and the next week on unpaid leave to think about what he'd done. To this day, he cannot look Sven or Makoto in the eye as they pass each other in the hallway. Makoto suspects he won't suffer long—only as long as it takes him to find another job. Maybe one with IT people who don't know what search keywords he uses. [Advertisement] Scale your release pipelines, creating secure, reliable, reusable deployments with one click. Download and learn more today!
|
 |
by Remy Porter on (#2X97T)
Processing financial transactions is not the kind of software you want to make mistakes in. If something is supposed to happen, it is definitely supposed to happen. Not partially happen. Not maybe happen.Thus, a company like Charles R’s uses a vendor-supplied accounting package. That vendor has a professional services team, so when the behavior needs to be customized, Charles’s company outsources that development to the vendor.Of course, years later, that code needs to get audited, and it’s about then that you find out that the vendor outsourced their “professional services†to the lowest bidder, creating a less-than-professional service result.If you want to make sure than when the country code is equal to "HND", you want to be really sure.
|
 |
by Remy Porter on (#2WYXT)
Max’s team moved into a new office, which brought with it the low-walled, “bee-hive†style cubicle partitions. Their project manager cheerfully explained that the new space “would optimize collaborationâ€, which in practice meant that every random conversation between any two developers turned into a work-stopping distraction for everyone else.That, of course, wasn’t the only change their project manager instituted. The company had been around for a bit, and their original application architecture was a Java-based web application. At some point, someone added a little JavaScript to the front end. Then a bit more. This eventually segregated the team into two clear roles: back-end Java developers, and front-end JavaScript developers.“Silos,†the project manager explained, “are against the ethos of collaboration. We’re all going to be full stack developers now.†Thus everyone’s job description and responsibilities changed overnight.Add an overly ambitious release schedule and some unclear requirements, and the end result is a lot of underqualified developers rushing to hit targets with tools that they don’t fully understand, in an environment that isn’t conducive to concentration in the first place.Max was doing his best to tune out the background noise, when Mariella stopped into Dalton’s cube. Dalton, sitting straight across from Max, was the resident “front-end expertâ€, or at least, he had been before everyone was now a full-stack developer. Mariella was a long-time backend JEE developer who hadn’t done much of the web portion of their application at all, and was doing her best to adapt to the new world.“Dalton, what’s the easiest way to get the minimum value of an array of numbers in JavaScript?†Mariella asked.Max did his best to ignore the conversation. He was right in the middle of a particularly tricky ORM-related bug, and was trying to figure out why one fetch operation was generating just awful SQL.“Hrmmmm…†Dalton said, tapping at his desk and adding to the distraction while he thought. “That’s a tough one. Oh! You should use a filter!â€â€œA filter, what would I filter on?â€Max combed through the JPA annotations that controlled their data access, cursing the “magic†that generated SQL queries, but as he started to piece it together, Dalton and Mariella continued their “instructional†session.“In the filter callback, you’d just check to see if each value is the lowest one, and if it is, return true, otherwise return false.†Dalton knocked out a little drum solo on his desk, to celebrate his cleverness.“But… I wouldn’t know which value is the lowest one, yet,†Mariella said.“Oh, yeah… I see what you mean. Yeah, this is a tricky one.â€Max traced through the code. Okay, so the @JoinColumn is CUST_ID, so why is it generating a LIKE comparison instead of an equals? Wait, I think I’ve-“Ah ha!†Dalton said, chucking Max’s train of thought off the rails and through an HO-scale village. “You just sort the array and take the first value!†*Thumpa thumpa tadatada* went Dalton’s little desk drum solo.“I guess that makes sense,†Mariella said.At this point, Max couldn’t stay out of the conversation. “No! Don’t do that. Use reduce. Sorting’s an n(lg n) operation.â€â€œHunh?†Dalton said. His fingers nervously hovered over his desk, ready to play his next drum solo once he had a vague clue what Max was talking about. “In logs in? We’re not doing logging…â€Max tried again, in simple English. “Sorting is slow. The computer does a lot of extra work to sort all the elements.â€â€œNo it won’t,†Dalton said. “It’ll just take the first element.â€â€œAhem.†Max turned to discover the project manager looming over his cube. “We want to encourage collaboration,†the PM said, sternly, “but right now, Max, you’re being disruptive. Please be quiet and let the people around you work.â€And that was how Dalton’s Minimum Finding Algorithm got implemented, and released as part of their production code base.[Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
|
 |
by Remy Porter on (#2WVHX)
Microsoft’s SQL Server Integration Services is an ETL tool that attempts to mix visual programming (for designing data flows) with the reality that at some point, you’re just going to need to write some code. Your typical SSIS package starts as a straightforward process that quickly turns into a sprawling mix of spaghetti-fied .NET code, T-SQL stored procedures, and developer tears.TJ L. inherited an SSIS package. This particular package contained a step where a C# sub-module needed to pass a date (but not a date-time) to the database. Now, this could be done easily by using C#’s date-handling objects, or even in the database by simply using the DATE type, instead of the DATETIME type.Instead, TJ’s predecessor took this route instead:
|
 |
by Remy Porter on (#2WNDN)
Once upon a time, a long long time ago, I got contracted to show a government office how to build and deliver applications… in Microsoft Access. I’m sorry. I’m so, so sorry. As horrifying and awful as it is, Access is actually built with some mechanisms to actually support that- you can break the UI and behavior off into one file, while keeping the data in another, and you can actually construct linked tables that connect to a real database, if you don’t mind gluing a UI made out of evil and sin to your “real†database.Which brings us to poor Alex Rao. Alex has an application built in Access. This application uses linked tables, which he wants to convert to local tables. The VBA API exposed by Access doesn’t give him any way to do this, so he came up with this solution…
|
 |
by Remy Porter on (#2WBJ7)
Requirements change all the time. A lot of the ideology and holy wars that happen in the Git processes camps arise from different ideas about how source control should be used to represent these changes. Which commit changed which line of code, and to what end? But what if your source control history is messy, unclear, or… you’re just not using source control?For example, let’s say you’re our Anonymous submitter, and find the following block of code. Once upon a time, this block of code enforced some mildly complicated rules about what dates were valid to pick for a dashboard display.Can you tell which line of code was in a reaction to a radically changed requirement?
|
 |
by Remy Porter on (#2W5YY)
Michael got a customer call, from a PHP system his company had put together four years ago. He pulled up the code, which thankfully was actually up to date in source control, and tried to get a grasp of what the system does.There, he discovered a… unique way to define functions in PHP:
|
 |
by Erik Gern on (#2W377)
Early magnetic storage was simple in its construction. The earliest floppy disks and hard drives used an iron (III) oxide surface coating a plastic film or disk. Later media would use cobalt-based surfaces, providing a smaller data resolution than iron oxide, but wouldn’t change much.Samuel H. never had think much about this until he met Micah.The Noisiest AlgorithmIn the fall of 1980, Samuel was a freshman at State U. The housing department had assigned him Micah as his roommate, assuming that since both were Computer Science majors, they would get along.On their first night together, Samuel asked why Micah kept throwing his books off the shelf onto the floor. “Oh, I just keep shuffling the books around until they’re in the right order,†Micah said.“Have you tried, I don’t know, taking out one book at a time, starting from the left?†Samuel asked. “Or sorting the books in pairs, then sorting pairs of pairs, and so on?†He had read about sorting algorithms over the summer.Micah shrugged, continuing to throwing books on the floor.Divided PrioritiesIn one of their shared classes, Samuel and Micah were assigned as partners on a project. The assignment: write a program in Altair BASIC that analyzes rainfall measurements from the university weather station, then displays a graph and some simple statistics, including the dates with the highest and lowest values.All students had access to Altair 8800s in the lab. They were given one 8“ floppy disk with the rainfall data, and a second for additional code. Samuel wanted to handle the data read/write code and leave the display to Micah, but Micah insisted on doing the data-handling code himself. â€I’ve learned a lot," he said. Samuel remembered the sounds of books crashing on the floor and flinched. Still, he thought the display code would be easier, so he let Micah at it.Samuel finished his half of the code early. Micah, though, was obsessed with Star Trek, a popular student-coded space tactics game, and waited until the day before to start work. “Okay, tonight, I promise,†he said, as Samuel left him in the computer lab at an Altair. As he left, he hard Micah close the drive, and the read-head start clacking across the disk.CorruptedThe next morning, Samuel found Micah still in the lab at his Altair. He was in tears. “The data’s gone,†he said. “I don’t know what I did. I started getting read errors around 1AM. I think the data file got corrupted somehow.â€Samuel gasped when Micah handed him the floppy cask. Through the read window in the cover, he could see transparent stripes in the disk. The magnetic write surface had been worn away, leaving the clear plastic backing.Micah explained. He had written his code to read the data file, find the lowest value, write it to an entirely new file, then mark the value in the original file as read. Then it would read the original file again, write another new file, and so on.Samuel calculated that, with Micah’s “algorithm,†the original file would be read and written to n–1 times, given n entries.Old Habits Die HardSamuel went to the professor and pleaded for a new partner, showing him the floppy with the transparent medium inside. Samuel was given full credit for his half of the program. Micah would have to write his entire program from scratch with a new copy of the data.Samuel left Micah for another roommate that spring. He didn’t see much of him, as the latter had left Computer Science to major in Philosophy. He didn’t hear about Micah again until a spring day in 1989, after he had finished his PhD.A grad student, who worked at the computer help desk, told Samuel about a strange man at the computer lab one night. He was despondent, trying to find someone who could help him recover his thesis from a 3 1/2" floppy disk. The student offered to help, and when the man handed him the disk, he pulled the metal tab aside to check for dust.Most of the oxide coating had been worn away, leaving thin, transparent stripes.[Advertisement] Release!is a light card game about software and the people who make it. Play with 2-5 people, or up to 10 with two copies - only $9.95 shipped!
|
 |
by Mark Bowytz on (#2VWZ0)
"As an Australian, I demand that they replace one of the two Belgiums with something to represent the quarter of the Earth they missed!" writes John A.
|
 |
by Alex Papadimoulis on (#2VT8X)
As our friends at HIRED will attest, finding a good workplace is tough, for both the employee and the employer. Fortunately, when it comes looking for developer talent, Inedo has a bit of an advantage: in addition to being a DevOps products company, we publish The Daily WTF.Not too long ago, I shared a Support Analyst role here and ended up hiring fellow TDWTF Ben Lubar to join the Inedo team. He's often on the front lines, supporting our customer base; but he's also done some interesting dev projects as well (including a Source Gear Vault to Git migration tool).Today, we're looking for another developer to work from our Cleveland office. Our code is all in .NET, but we have a lot of integrations; so if you can write C# fairly comfortably but know Docker really well, then that's a great fit. The reason is that, as a software product company that builds tools for other developers, you'll do more than just write C# - in fact, a big part of the job will be resisting the urge to write mountains of code that don't actually solve a real problem. More often than not, a bit of support, a tutorial, an extension/plug-in, and better documentation go a heck of a lot further than new core product code.We do have a couple of job postings for the position (one on Inedo.com, the other on Indeed), and you're welcome to read those to get a feel for the actual bullet points. But if you're reading this and are interested in learning more, you can use the VIP line and bypass the normal process: just shoot me an email directly at apapadimoulis at inedo dot com with "[TDWTF/Inedo] .NET Developer" as the subject and your resume attached.Oh, we're also looking for a Community Manager, to help with both The Daily WTF and Inedo communities. So if you know anyone who might be interested in that, send them my way![Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
|
 |
by Alex Papadimoulis on (#2VYB6)
As our friends at HIRED will attest, finding a good workplace is tough, for both the employee and the employer. Fortunately, when it comes looking for developer talent, Inedo has a bit of an advantage: in addition to being a DevOps products company, we publish The Daily WTF.Not too long ago, I shared a Support Analyst role here and ended up hiring fellow TDWTF Ben Lubar to join the Inedo team. He's often on the front lines, supporting our customer base; but he's also done some interesting dev projects as well (including a Source Gear Vault to Git migration tool).Today, we're looking for another developer to work from our Cleveland office. Our code is all in .NET, but we have a lot of integrations; so if you can write C# fairly comfortably but know Docker really well, then that's a great fit. The reason is that, as a software product company that builds tools for other developers, you'll do more than just write C# - in fact, a big part of the job will be resisting the urge to write mountains of code that don't actually solve a real problem. More often than not, a bit of support, a tutorial, an extension/plug-in, and better documentation go a heck of a lot further than new core product code.We do have a couple of job postings for the position (one on Inedo.com, the other on Indeed), and you're welcome to read those to get a feel for the actual bullet points. But if you're reading this and are interested in learning more, you can use the VIP line and bypass the normal process: just shoot me an email directly at apapadimoulis at inedo dot com with "[TDWTF/Inedo] .NET Developer" as the subject and your resume attached.Oh, we're also looking for a Community Manager, to help with both The Daily WTF and Inedo communities. So if you know anyone who might be interested in that, send them my way![Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
|
 |
by Jane Bailey on (#2VSZ6)
Here's how open-source is supposed to work: A goup releases a product, with the source code freely available. Someone finds a problem. They solve the problem, issue a pull request, and the creators merge that into the product, making it better for everyone.Here's another way open-source is supposed to work: A group releases a product, with the source code freely available. Someone finds a problem, but they can't fix it themselves, so they issue a bug report. Someone else fixes the problem, issues a pull request, and the creators merge that into the product, making it better for everyone.Here's one way open-source works: Someone creates a product. It gets popular—and I mean really, really popular, practically overnight. The creator didn't ask for this. They have no idea what to do with success. They try their best to keep up, but they can't keep on top of everything all the time. They haven't even set up a build pipeline yet. They're flying by the seat of their pants. One day, unwisely choosing to program with a fever, they commit broken code and push it up to GitHub, triggering an automatic release. Fifteen thousand downstram dependencies find their build broken and show up to scold the creator for not running tests before releasing.Here's another way open-source works: A group creates a product. It gets popular. Some time later, there are 600 open issues and over 50 pending pull requests. The creator hasn't commented in a year, but people keep vainly trying to improve the product.Here's another way open-source works: A group creates a product. They decide to avoid the above PR disaster by using some off-site bug tracker. Someone files a bug. Then another bug. Then 5 or 10 more. The creator goes on a rampage, insisting that everyone is using it wrong, and deletes all the bug reports, banning the users who submitted them. The product continues to gain success, and more and more people file bugs, only to find the bug reports summarily closed. Sometimes people get lucky and their reports will be closed, then re-opened when another dev decides to fix the problem.Here's another way open-source works: Group A creates a product. Group B creates a product, and uses the first product as their support forum. That forum gets hacked. Group B files a bug to Group A, rightly worried about the security of the software they use. After all, if the forum has a remote code exploit, maybe they should move to something newer, maybe written in Ruby instead of PHP. One of the developers from Group A, today's submitter, offers to investigate.Many forums allow admins to edit the themes for the site directly; for example, NodeBB provides admins a textbox in which they can paste CSS to tweak the theme to their liking. This forum figures that since the admins are already on the wrong side of the airtight hatchway, they can inject bits of PHP code directly into the forum header. Code like, say, saving a poison payload to a disk that creates a endpoint that accepts arbitrary file uploads so they can root the box.But how did the hacker get access to that admin panel? Surely that's a security flaw, right? Turns out they'd found a weak link in the security chain and applied just enough force to break their way in. If you work in security, I'm sure you won't be surprised to hear the flaw: one of the admins had a weak password, one right out of a classic dictionary list.Here's another way open-source works: 15% of the NPM ecosystem was controlled by people with weak passwords. Someone hacks them all, tells NPM how they did it, and gets a mass forced-reset on everyone's passwords. Everyone is more secure. [Advertisement] Universal Package Manager – store all your Maven, NuGet, Chocolatey, npm, Bower, TFS, TeamCity, Jenkins packages in one central location. Learn more today!
|
 |
by Jane Bailey on (#2VYB7)
Here's how open-source is supposed to work: A goup releases a product, with the source code freely available. Someone finds a problem. They solve the problem, issue a pull request, and the creators merge that into the product, making it better for everyone.Here's another way open-source is supposed to work: A group releases a product, with the source code freely available. Someone finds a problem, but they can't fix it themselves, so they issue a bug report. Someone else fixes the problem, issues a pull request, and the creators merge that into the product, making it better for everyone.Here's one way open-source works: Someone creates a product. It gets popular—and I mean really, really popular, practically overnight. The creator didn't ask for this. They have no idea what to do with success. They try their best to keep up, but they can't keep on top of everything all the time. They haven't even set up a build pipeline yet. They're flying by the seat of their pants. One day, unwisely choosing to program with a fever, they commit broken code and push it up to GitHub, triggering an automatic release. Fifteen thousand downstram dependencies find their build broken and show up to scold the creator for not running tests before releasing.Here's another way open-source works: A group creates a product. It gets popular. Some time later, there are 600 open issues and over 50 pending pull requests. The creator hasn't commented in a year, but people keep vainly trying to improve the product.Here's another way open-source works: A group creates a product. They decide to avoid the above PR disaster by using some off-site bug tracker. Someone files a bug. Then another bug. Then 5 or 10 more. The creator goes on a rampage, insisting that everyone is using it wrong, and deletes all the bug reports, banning the users who submitted them. The product continues to gain success, and more and more people file bugs, only to find the bug reports summarily closed. Sometimes people get lucky and their reports will be closed, then re-opened when another dev decides to fix the problem.Here's another way open-source works: Group A creates a product. Group B creates a product, and uses the first product as their support forum. That forum gets hacked. Group B files a bug to Group A, rightly worried about the security of the software they use. After all, if the forum has a remote code exploit, maybe they should move to something newer, maybe written in Ruby instead of PHP. One of the developers from Group A, today's submitter, offers to investigate.Many forums allow admins to edit the themes for the site directly; for example, NodeBB provides admins a textbox in which they can paste CSS to tweak the theme to their liking. This forum figures that since the admins are already on the wrong side of the airtight hatchway, they can inject bits of PHP code directly into the forum header. Code like, say, saving a poison payload to a disk that creates a endpoint that accepts arbitrary file uploads so they can root the box.But how did the hacker get access to that admin panel? Surely that's a security flaw, right? Turns out they'd found a weak link in the security chain and applied just enough force to break their way in. If you work in security, I'm sure you won't be surprised to hear the flaw: one of the admins had a weak password, one right out of a classic dictionary list.Here's another way open-source works: 15% of the NPM ecosystem was controlled by people with weak passwords. Someone hacks them all, tells NPM how they did it, and gets a mass forced-reset on everyone's passwords. Everyone is more secure. [Advertisement] Universal Package Manager – store all your Maven, NuGet, Chocolatey, npm, Bower, TFS, TeamCity, Jenkins packages in one central location. Learn more today!
|
 |
by Remy Porter on (#2VPZ3)
Blane D is responsible for loading data into a Vertica 8.1 database for analysis. Vertica is a distributed, column-oriented store, for data-warehousing applications, and its driver has certain quirks.For example, a common task that you might need to perform is swapping storage partitions around between tables to facilitate bulk data-loading. Thus, there is a SWAP_PARTITIONS_BETWEEN_TABLES() stored procedure. Unfortunately, if you call this function from within a prepared statement, one of two things will happen: the individual node handling the request will crash, or the entire cluster will crash.No problem, right? Just don’t use a prepared statement. Unfortunately, if you use the ODBC driver for Python, every statement is converted to a prepared statement. There’s a JDBC driver, and a bridge to enable it from within Python, but it also has that problem, and it has the added cost of requiring a a JVM running.So Blane did what any of us would do in this situation: he created a hacky-workaround that does the job, but requires thorough apologies.
|
 |
by Remy Porter on (#2VYB8)
Blane D is responsible for loading data into a Vertica 8.1 database for analysis. Vertica is a distributed, column-oriented store, for data-warehousing applications, and its driver has certain quirks.For example, a common task that you might need to perform is swapping storage partitions around between tables to facilitate bulk data-loading. Thus, there is a SWAP_PARTITIONS_BETWEEN_TABLES() stored procedure. Unfortunately, if you call this function from within a prepared statement, one of two things will happen: the individual node handling the request will crash, or the entire cluster will crash.No problem, right? Just don’t use a prepared statement. Unfortunately, if you use the ODBC driver for Python, every statement is converted to a prepared statement. There’s a JDBC driver, and a bridge to enable it from within Python, but it also has that problem, and it has the added cost of requiring a a JVM running.So Blane did what any of us would do in this situation: he created a hacky-workaround that does the job, but requires thorough apologies.
|
 |
by Mark Bowytz on (#2VMHK)
|
 |
by Alex Papadimoulis on (#2VHYS)
|
 |
by Alex Papadimoulis on (#2VYBA)
|
 |
by Mark Bowytz on (#2VB3Q)
"Truly the best null I've ever had. Definitely would purchase again," wrote Andrew R.
|
 |
by Remy Porter on (#2V81J)
In addition to our “bread and butter†of bad code, bad bosses, worse co-workers and awful decision-making, we always love the chance to turn out occassional special events. This time around, our sponsors at Hired gave us the opportunity to build and film a sketch.I’m super-excited for this one. It’s a bit more ambitious than some of our previous projects, and pulled together some of the best talent in the Pittsburgh comedy community to make it happen. Everyone who worked on it- on set or off- did an excellent job, and I couldn't be happier with the results.Once again, special thanks to Hired, who not only helped us produce this sketch, but also helps keep us keep the site running. With Hired, instead of applying for jobs, your prospective employer will apply to interview you. You get placed in control of your job search, and Hired provides a “talent advocate†who can provide unbiased career advice and make sure you put your best foot forward. Sign up now, and find the best opportunities for your future with Hired. And now, our feature presentation: The AgreementBrought to you by:
|
 |
by Remy Porter on (#2VYBC)
In addition to our “bread and butter†of bad code, bad bosses, worse co-workers and awful decision-making, we always love the chance to turn out occassional special events. This time around, our sponsors at Hired gave us the opportunity to build and film a sketch.I’m super-excited for this one. It’s a bit more ambitious than some of our previous projects, and pulled together some of the best talent in the Pittsburgh comedy community to make it happen. Everyone who worked on it- on set or off- did an excellent job, and I couldn't be happier with the results.Once again, special thanks to Hired, who not only helped us produce this sketch, but also helps keep us keep the site running. With Hired, instead of applying for jobs, your prospective employer will apply to interview you. You get placed in control of your job search, and Hired provides a “talent advocate†who can provide unbiased career advice and make sure you put your best foot forward. Sign up now, and find the best opportunities for your future with Hired. And now, our feature presentation: The AgreementBrought to you by:
|
 |
by Remy Porter on (#2V4X6)
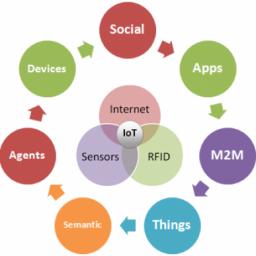
Folks, we’ve got to talk about some of the headlines about the Internet of “Thingsâ€. If you’ve been paying even no attention to that space, you know that pretty much everything getting released is some combination of several WTFs, whether in conception, implementation, and let’s not forget security.I get it. It’s a gold-rush business. We’ve got computers that are so small, so cheap, and so power-efficient, that we can slap the equivalent of a 1980s super-computer in a toilet seat. There's the potential to create products that make our lives better, that make the world better, and could carry us into a glowing future. It just sometimes feels like that's not what anybody's actually trying to make, though. Without even checking, I’m sure you can buy a WiFi enabled fidget spinner that posts the data to a smartphone app where you can send “fidges†to your friends, bragging about your RPMs.We need this news-roundup, because when Alexa locks you out of your house because you didn’t pay for Amazon Prime this month, we can at least say “I told you soâ€. You think I’m joking, but Burger King wants in on that action, with its commercial that tries to trick your Google Assistant into searching for burgers. That’s also not the first time that a commercial has trigged voice commands, and I can guarantee that it isn’t going to be the last.Now, maybe this is sour grapes. I bought a Nest thermostat before it was cool, and now three hardware generations on, I’m not getting software updates, and there are rumors about the backend being turned off someday. Maybe Nest needs a model more like “Hive Hubâ€. Hive is a startup with £500M invested, making it one of the only “smart home†companies with an actual business model. Of course, that business model is that you’ll pay $39.99 per month to turn your lights on and off.At least you know that some of that money goes to keeping your smart-home secure. I’m kidding, of course- nobody spends any effort on making these devices secure. There are many, many high profile examples of IoT hacks. You hook your toaster up to the WiFi and suddenly it’s part of a botnet swarm mining BitCoins. One recent, high-profile example is the ZigBee Protocol, which powers many smart-home systems. It’s a complete security disaster, and opens up a new line of assault- instead of tricking a target to plug a thumb drive into their network, you can now put your payload in a light bulb.Smart-homes aside, IoT in general is breeding ground for botnets. Sure, your uncle Jack will blindly click through every popup and put his computer password in anything that looks like a password box, but at least you can have some confidence that his Windows/Mac/Linux desktop has some rudimentary protections bundled with the OS. IoT vendors apparently don’t care.Let’s take a break, and take a peek at a fun story about resetting a computerized lock. Sure, they could have just replaced the lock, but look at all the creative hackery they had to do to get around it.With that out of the way, let’s talk about tea. Ever since the Keurig coffee maker went big, everyone’s been trying to be “the Keurig for waffles†or “the Keurig for bacon†or “the Keurig for juiceâ€- the latter giving us the disaster that is the Juicero. Mash this up with the Internet of Things, and you get this WiFi enabled tea-maker, which can download recipes for brewing tea off the Internet. And don’t worry, it’ll always use the correct recipe because each pod is loaded with an RFID that not only identifies which recipe to use, but ensures that you’re not using any unathorized tea.In addition to the “Keurig, but for $X,†there’s also the ever popular “the FitBit, but for $X.†Here’s the FitBit for desks. It allows your desk to nag you about getting up, moving around, and it’ll upload your activity to the Internet while it’s at it. I’m sure we’re all really excited for when our “activity†gets logged for future review.Speaking of FitBits, Qualcomm just filed some patents for putting that in your workout shoes. This is actually not a totally terrible idea- I mean, by standards of that tea pot, anyway. I share it here because they’re calling it “The Internet of Shoes†which is a funny way of saying, “our marketing team just gave upâ€.Finally, since we’re talking about Internet connected gadgets that serve no real purpose, Google Glass got its first software update in three years. Apparently Google hasn’t sent the Glass to a farm upstate, where it can live with Google Reader, Google Wave, Google Hangouts, and all the other projects Google got bored of. [Advertisement] Application Release Automation – build complex release pipelines all managed from one central dashboard, accessibility for the whole team. Download and learn more today!
|
 |
by Charles Robinson on (#2V1VM)
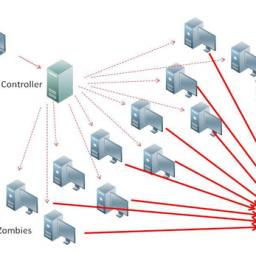
Joe K was a developer at a company that provided a SaaS Natural Language Processing system. As Chief Engineer of the Data Science Team (a term that make him feel like some sort of mad professor), his duties included coding the Data Science Service. It provided the back-end for handling the complex, heavy-lifting type of processing that had to happen in real-time. Since it was very CPU-intensive, Joe spent a lot of time trying to battle latency. But that was the least of his problems.The rest of the codebase was a cobbled-together mess that had been coded by the NLP researchers- scientists with no background in programming or computer science. Their mantra was “If it gets us the results we need, who cares how it looks behind the scenes?†This meant Joe’s well-designed data service somehow had to interface with applications made from a pile of ugly hacks. It was difficult at times, but he managed to get the job done while also keeping CPU usage to a minimum.One day Joe was working away when Burt, the company CEO, burst in to their humble basement computer lab in an obvious tizzy. Burt rarely visited the “egghead dungeonâ€, as he called it, so something had to be amiss. “JOE!†he cried out. “The production data science service is completely down! Every customer we have gave me an angry call within the last ten minutes!â€Considering this was an early-stage startup with only five customers, Burt’s assertion was probably true, if misleading. “Wow, ok Burt. Let me get right on that!†Joe offered, feeling flustered. He took a look at the error logging service and there was nothing to be found. He then attempted to SSH to each of the production servers, with success. He decided to check performance on the servers and an entire string of red flags shot straight up the proverbial flag pole. Every production server was at 100% CPU usage.“I have an effect for you, Burt, but not a cause. I’ll have to dig deeper but it almost seems like… a Denial of Service attack?†Joe offered, not believing that would actually be the case. With only five whitelisted customers able to connect, all of them using the NLP system to its fullest shouldn’t come even close to causing this.While looking further at the server logs, Joe got an instant message from Xander, the software engineer who worked on the dashboards, “Hey Joe, I noticed prod was down… could it be related to something I’m doing?â€â€œUmmm… maybe? What is it you are doing exactly?†Joe replied, with a new sense of concern. Xander’s dashboard shouldn’t have any interaction with the DSS, so it seemed like an odd question. Requests to the NLP site would initially come to a front-end server, and if there was some advanced analysis that needed to happen, that server would RPC to the DSS. After the response was computed, the front-end server would log the request and response to the Xander’s dashboard system so it could monitor usage stats.“Well, the dashboard is out of sync,†Xander explained. There had been a bug causing events to not make it to the dashboard system for the past month. They would need to be added to make the dashboard accurate. This could have been a simple change to the dashboard’s database, but instead Xander decided to replay all of the actual HTTP requests to the front end. Many of those requests triggered processing on the DSS- processing which had already been done. And since it was taking a long time, Xander had batched up the resent requests and was running them from three different machines, thus providing a remarkably good simulation of a DDoS.“STOP YOUR PROCESS IMMEDIATELY AND DO THIS THE RIGHT WAY!†Joe shot back, all caps intended.“Ok, ok, sorry. I’ll get this cleaned up,†Xander assured Joe. Within 15 minutes, the server CPU usage returned to normal levels and everything was great again. Joe was able to get Burt off his back and return to his normal duties.A few minutes later, Joe’s IM dinged again with a message from Xander. "Hey Joe, sorry about that, LOL. But are we 100% sure that was the problem? Should I do it again just to be sure?If there was a way for Joe to use instant messaging to send a virtual strangulation to Xander, he would have done it. But a “HELL NO!!!†would have to suffice.[Advertisement] Release!is a light card game about software and the people who make it. Play with 2-5 people, or up to 10 with two copies - only $9.95 shipped!
|
 |
by Ellis Morning on (#2TYQM)
Today, submitter Adam shows us how thoughtless language assumptions made by programmers are also hilarious language assumptions:
|
 |
by Ellis Morning on (#2TMN8)
Shawn W. was a newbie support tech at a small company. Just as he was beginning to familiarize himself with its operational quirks, he got a call from Jim: The Big Boss.Dread seized Shawn. Aside from a handshake on Interview Day, the only "interaction" he'd had with Jim thus far was overhearing him tear into a different support rep about having to deal with "complicated computer crap" like changing passwords. No doubt, this call was bound to be a clinic in saintly patience."Tech Support," Shawn greeted. "How may—?""I'm out of space and I need more!" Jim barked over the line."Oh." Shawn mentally geared up for a memory or hard drive problem. "Did you get a warning or error mes—?""Just get up here and bring some more space with you!" Jim hung up."Oh, boy," Shawn muttered to himself.Deciding that he was better off diagnosing the problem firsthand, Shawn trudged upstairs to Jim's office. To his pleasant surprise, he found it empty. He sank into the cushy executive-level chair. Jim hadn't been away long enough for any screensavers or lock screens to pop up, so Shawn had free rein to examine the machine.There wasn't much to find. The only program running was a web browser, with a couple of tabs open to ESPN.com and an investment portfolio. The hardware itself was fairly new. CPU, memory, hard drive all looked fine."See, I'm out of space. Did you bring me more?"Shawn glanced up to find Jim barreling toward him, steaming mug of coffee in hand. He braced himself as though facing down an oncoming freight train. "I'm not sure I see the problem yet. Can you show me what you were doing when you noticed you needed more space?"Jim elbowed his way over to the mouse, closed the browser, then pointed to the monitor. "There! Can't you see I'm out of space?"Indeed, Jim's desktop was full. So many shortcuts, documents, widgets, and other icons crowded the screen that the tropical desktop background was barely recognizable as such.While staring at what resembled the aftermath of a Category 5 hurricane, Shawn debated his response. "OK, I see what you mean. Let's see if we can—""Can't you just get me more screen?" Jim pressed.More screen? "You mean another monitor?" Shawn asked. "Well, yes, I could add a second monitor if you want one, but we could also organize your desktop a little and—""Good, get me one of those! Don't touch my icons!" Jim shooed Shawn away like so much lint. "Get out of my chair so I can get back to work."A short while later, Shawn hooked up a second monitor to Jim's computer. This prompted a huge and unexpected grin from the boss. "I like you, you get things done. Those other guys would've taken a week to get me more space!"Shawn nodded while stifling a snort. "Let me know if you need anything else."Once Jim had left for the day, Shawn swung past the boss' office out of morbid curiosity. Jim had already scattered a few dozen shortcuts across his new real estate. Another lovely vacation destination was about to endure a serious littering problem.[Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
|
 |
by Remy Porter on (#2THGQ)
The innermost circle of Hell, as we all know, is trying to resolve printer driver issues for all eternity. Ben doesn’t work with the printers that we mere mortals deal with on a regular basis, though. He runs a printing press, three stories of spinning steel and plates and ink and rolls of paper that could crush a man.Like most things, the press runs Linux- a highly customized, modified version of Linux. It’s a system that needs to be carefully configured, as “disaster recovery†has a slightly different meaning on this kind of heavy equipment. The documentation, while thorough and mostly clear, was obviously prepared by someone who speaks English as a second language. Thus, Ben wanted to check the shell scripts to better understand what they did.The first thing he caught was that each script started with variable declarations like this:
|
 |
by Jane Bailey on (#2TE9G)
Contracting can be really hit or miss. Sometimes, you're given a desk and equipment and treated just like an employee, except better paid and exempt from team-building exercises. Sometimes, however, you're isolated in your home office, never speaking to anyone, working on tedious, boring crap they can't convince their normal staff to do.Eric was contracted to perform basic website updating tasks for a government agency. Most of the work consisted of receiving documents, uploading them to the server, and adding them to a page. There were 4 document categories, each one organized by year. Dull as dishwater, but easy.The site was hosted by a third party in a shared hosting environment. It ran on a CMS produced by another party. WTFCMS was used in many high-profile sites, so the agency figured it had to be good. Eric was given login credentials and—in the way of techies given boring tasks everywhere—immediately began automating the task at hand.Step 1 of this automation was to get a list of articles with their IDs. Eric was pleased to discover that the browser-based interface for the CMS used a JSON request to get the list of pages. With the help of good old jq, he soon had that running in a BASH shell script. To get the list of children for an article, he passed the article's ID to the getChildren endpoint.Usually, in a heirarchy like this, there's some magic number that means "root element." Eric tried sending a series of likely candidates, like 0, -1, MAX_INT, and MIN_INT. It turned out to be -1 ... but he also got a valid list when he passed in 0.Curious, he thought to himself. This appears to be a list of articles ... and hey, here's the ones I got for this site. These others ...? No way.Sure enough, passing in a parent ID of 0 had gotten Eric some sort of super-root: every article across every site in the entire CMS system. Vulnerability number 1.Step 2 was to take the ID list and get the article data so he could associate the new file with it. This wasn't nearly as simple. There was no good way to get the text of the article from the JSON interface; the CMS populated the articles server-side.Eric was in too deep to stop now, though. He wrote a scraper for the edit page, using an XML parser to handle the HTML form that held the article text. Once he had the text, he compared it by hand to the POST request sent from his Firefox instance to ensure he had the right data.And he did ... mostly. Turns out, the form was manipulated by on-page Javascript before being submitted: fields were disabled or enabled, date/time formats were tweaked, and the like. Eric threw together some more scripting to get the job done, but now he wasn't sure if he would hit an edge case or somehow break the database if he ran it. Still, he soldiered on.Step 3 was to upload the files so they could be linked to the article. With Firebug open, Eric went about adding an upload.Now, WTFCMS seemed to offer the usual flow: enter a name, select a file, and click Upload to both upload the file and save it as the given name. When he got to step 2, however, the file was uploaded immediately—but he still had to click the Upload button to "save" it.What happens if I click Cancel? Eric wondered. No, never mind, I don't want to know. What does the POST look like?It was a mess of garbage. Eric was able to find the file he uploaded, and the name he'd given it ... and also a bunch of server-side information the user shouldn't be privvy to, let alone be able to tamper with. Things like, say, the directory on the server where the file should be saved. Vulnerability number 2.The response to the POST contained, unexpectedly, HTML. That HTML contained an iframe. The iframe contained an iframe. iframe contained iframe; iframe contained a form. In that form were two fields: a submit button, reading "Upload", and a hidden form field containing the path of the uploaded file. In theory, he could change that to read anything on the server. Now he had both read and write access to any arbitrary destination in the CMS, maybe even on the server itself. Vulnerability number 3.It was at this point that Eric gave up on his script altogether. This is the kind of task that Selenium IDE is perfect for. He just kept his head down, hoped that the server had some kind of validation to prevent curious techies like himself from actually exploiting any of these potential vulnerabilities, and served out the rest of his contract.[Advertisement] Release!is a light card game about software and the people who make it. Play with 2-5 people, or up to 10 with two copies - only $9.95 shipped!
|
 |
by Remy Porter on (#2TB96)
For a brief period of time, say, about 3–4 years ago, if you wanted to sound really smart, you’d bring up “functional programmingâ€. Name-dropping LISP or even better, Haskell during an interview marked you as a cut above the hoi polloi. Even I, surly and too smart for this, fell into the trap of calling JavaScript “LISP with curly bracesâ€, just because it had closures.Still, functional programming features have percolated through other languages because they work. They’re another tool for the job, and like any tool, when used by the inexpert, someone might lose a finger. Or perhaps someone should lose a finger, if only as a warning to others.For example, what if you wanted to execute a loop 100 times in JavaScript? You could use a crummy old for loop, but that’s not functional. The functional solution comes from an anonymous submitter:
|
 |
by Mark Bowytz on (#2T4BE)
"I asked my son, @Firstname, and he is indeed rather @Emotion about going to @ThemePark!" wrote Chris @LASTNAME.
|
 |
by Mark Bowytz on (#2T1CR)
|
 |
by Alex Papadimoulis on (#2SXSF)
|
 |
by Alex Papadimoulis on (#2SSR0)
|
 |
by Alex Papadimoulis on (#2SNS4)
|
 |
by Mark Bowytz on (#2SCBS)
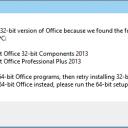
"I know software can't always be perfect, but things like this make me want to shut down my PC and say that's enough computering for the day," writes Timothy W.
|