 |
by Mark Bowytz on (#2RKMP)
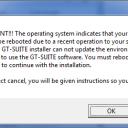
John A. wrote, "Wait, so 'Cancel' is 'Continue' and 'OK' is really 'Cancel'!?"
|
 The Daily WTF
The Daily WTF
| Link | http://thedailywtf.com/ |
| Feed | http://syndication.thedailywtf.com/TheDailyWtf |
| Updated | 2026-02-28 08:46 |
 |
by Remy Porter on (#2RFMN)
Twelve years ago, a company decided they needed a website. They didn’t have any web developers, and they didn’t want to hire any, so they threw a PHP manual at the new hire who happened to “be good with computersâ€, and called it a day.Ms. “Good With Computers†actually learned something from the experience, and moved on to a lucrative career in web development. Unfortunately, she left behind the code she learned by doing, and now Bert has been brought in to clean up the code.Take this block, which translates an airport code into a location name…
|
 |
by Erik Gern on (#2RBCE)
Fresh out of college and out of money, Johan K. started work at Midgard Manufacturing as a junior developer. His supervisor Ragna made it clear: he would only be responsible for coding error handlers.“Our plant equipment is several decades old,†she said, “and we have to rely on the manufacturer-provided documentation for adequate coverage. To be honest, none of the senior developers want to bother. So instead of bothering one of them, you’ll be doing it.â€Johan didn’t have a problem with this. He knew he’d have to earn his chops at Midgard. But after he was given the stack of manuals that towered over his monitor, he wondered just how long it would take.Pride Goeth Before a FallOne month later, he had made it through a hundred pages of the first manual. Ragna checked in periodically, more interested in how complete his code was than how quickly he was getting through his list of error conditions.The manual he was working on was for a steel press. Vintage 1985, the steel press’s firmware - using Microsoft Xenix - relied on the flakiest of communication protocols: passing information via temp file. Every night around 2AM, the press would go down for maintenance. A shell script, written by Johan, would read data from the temp file the steel press had created, enter it into a SQL database, then delete the file from disk.Half the lines of code in Johan’s script were if/then blocks, one for each condition listed in the manual.
|
 |
by Remy Porter on (#2R77W)
Interviewing developers always poses a challenge. You can’t rate their skills at writing code without seeing them write code, and most of the code they’ve written probably belongs to someone else. Writing anything non-trivial takes time, which both the candidate and the interviewer may not be willing to spend. Even then, it’s not always representative. And let’s not even talk about whiteboard programming.Douglas’s company makes a compromise- they’ll give a time-boxed programming challenge. A developer is given two hours, access to the Internet, and a moderately complex problem. A smart developer might make some mistakes on the trickier parts of the problems, which is great, because it doesn’t fail them- it shows how they think. One candidate, Steve, never quite got that far.At one point in the process, the code needs to determine if two dates are within 90 days of each other. Even in Java, this is a trivial task, worthy of one line of code. Possibly two, if you want to be super clear:
|
 |
by Alex Papadimoulis on (#2R3SD)
|
 |
by Mark Bowytz on (#2QTF0)
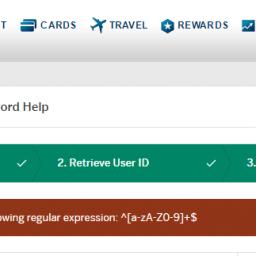
"Apparently, if AMEX's site knows that you're a developer, it will present a REGEX challenge before allowing you to reset your password," Jim wrote.
|
by Remy Porter on (#2QPJT)
Tim joined a company that provided a SaaS solution for tracking attendance and grades in schools. The job was mostly minor updates to a ColdFusion application, although there was an active project to replace it with something more modern. Tim felt like half of his hiring was based on him knowing when to throw out buzzwords like SPA or REST or Reactive Programming.“It’s not the first time,†Karmen explained. She’d been with the company for some time. “When I joined, they had just upgraded to ColdFusion from a VBA hack on Microsoft Access. Crazy days, back then, when the whole ‘selling service, not software’ thing was new. Sometimes, I think I was hired because I knew the right buzzwords.â€Ostensibly, Karmen and Tim were meant to be focused on the new version of the application, but the ColdFusion version was so old and so poorly maintained that they spent 75% of their time in firefighting mode. The rest of the team had neatly adapted to the culture of “just put out the fire, and don’t worry about code quality, there’ll be a new fire tomorrowâ€, which of course only created more fires to put out.One day, near the end of the month, the webmaster inbox had an alert message from their webhost.
 |
by Jane Bailey on (#2QJKB)
Recently, at my dayjob, I had a burning need to understand how scheduled tasks work. You see, we've recently switched from Adobe Coldfusion to Lucee, and I was shaky on how Adobe did things before, so I wanted a deeper understanding of how the code I was working on would be executed. For the uninitiated, Lucee is an open-source reimplementation of Cold Fusion. And that's not the WTF.It's open source, I thought to myself. I'll just take a look at the code.I had one problem. Then I looked at the code. Now I have two problems ... and a headache:
|
 |
by Remy Porter on (#2QE8D)
Rachel started working as a web developer for the local bus company. The job made her feel young, since the buses, the IT infrastructure, and most of their back-office code was older than she was. The bus fare-boxes were cash only, and while you could buy a monthly pass, it was just a little cardboard slip that you showed the driver. Their accounting system ran on a mainframe, their garage management software was a 16-bit DOS application. Email ran on an Exchange 5.5 server.In charge of all of the computing systems, from the web to DOS, was Virgil, the IT director. Virgil had been hired back when the accounting mainframe was installed, and had nestled into his IT director position like a tick. The bus company, like many such companies in the US, was ostensibly a private company, but chartered and subsidized by the city. This created a system which had all the worst parts of private-sector and public-sector employment merged together, and Virgil was the master of that system.Rachel getting hired on was one of his rare “lossesâ€, and he wasn’t shy about telling her so.“I’ve been doing the web page for years,†Virgil said. “It has a hit counter, so you can see how many hits it actually gets- maybe 1 or 2 a week. But management says we need to have someone dedicated to the website.†He grumbled. “Your salary is coming out of my budget, you know.â€That website was a FrontPage 2000 site, and the hit-counter was broken in any browser that didn’t have ActiveX enabled. Rachel easily proved that there was far more traffic than claimed, not that there was a lot. And why should there be? You couldn’t buy a monthly pass online, so the only feature was the ability to download PDFs of the hand-schedules.With no support, Rachel did her best to push things forward. She redesigned the site to be responsive. She convinced the guy who maintained their bus routes (in a pile of Excel spreadsheets) to give her regular exports of the data, so she could put the schedules online in a usable fashion. Virgil constantly grumbled about wasting money on a website nobody used, but as she made improvements, more people started using it.Then it was election season. The incumbent mayor had been complaining about the poor service the bus company was offering, the lack of routes, the costs, the schedules. His answer was, “cut their fundingâ€. Management started talking about belt-tightening, Virgil started dropping hints that Rachel was on the chopping block, and she took the hint and started getting resumes out.A miracle occurred. The incumbent mayor’s campaign went off the rails. He got caught siphoning money from the city to pay for private trips. A few local cops mentioned that they’d been called in to cover-up the mayor’s frequent DUIs. His re-election campaign’s finances show strange discrepancies, and money had come in that couldn’t be tied back to a legitimate contribution. He tried to get a newly built stadium named after himself, which wasn’t illegal, but was in poor taste and was the final straw. He dropped out of the election, paving the way for “Mayor Fred†to take over. Mayor Fred was a cool Mayor. He wanted to put in bike lanes. He wanted to be called “Mayor Fredâ€. He wanted to make it easier for food trucks to operate in the city. And while he shared his predecessor’s complaints about the poor service from the bus company, he had a different solution, which he revealed while taking a tour of the bus company’s offices.“I’m working right now to secure federal grants, private sector funding, to fund a modernization project,†Mayor Fred said, grinning from behind a lectern. “Did you know we’re paying more to keep our old buses on the road for five years than it would cost to buy new buses?†And thus, Mayor Fred made promises. Promises about new buses, promises about top-flight consultants helping them plan better routes, promises about online functionality.Promises that made Virgil grumble and whine. Promises that the mayor… actually kept. New buses started to hit the streets. They had GPS and a radio communication system that gave them up-to-the-second location reporting. Rachel got put in charge of putting that data on the web, with a public API, and tying it to their schedules. A group of consultants swung through to help, and when the dust settled, Rachel’s title was suddenly “senior web developer†and she was in charge of a team of 6 people, integrating new functionality to the website.Virgil made his opinion on this subject clear to her: “You are eating into my budget!â€â€œIsn’t your budget way larger?†Rachel asked.“Yes, but there’s so much more to spend it on! We’re a bus company, we should be focused on getting people moving, not giving them pretty websites with maps that tell them where the buses are! And now there’s that new FlashCard project!â€FlashCard was a big project that didn’t involve Rachel very much. Instead of cash fares and cardboard passes, they were going to get an RFID system. You could fill your card at one of the many kiosks around the city, or even online. “Online†of course, put it in Rachel’s domain, but it was mostly a packaged product. Virgil, of all people, had taken over the install and configuration, Rachel just customized the stylesheet so that it looked vaguely like their main site.Rachel wasn’t only an employee of the bus company, she was also a customer. She was one of the first in line to get a FlashCard. For a few weeks, it was the height of convenience. The stop she usually needed had a kiosk, she just waved her card at the farebox and paid. And then, one day, when her card was mostly empty and she wasn’t anywhere near a kiosk, she decided to try filling her card online.
|
 |
by Ellis Morning on (#2QADJ)
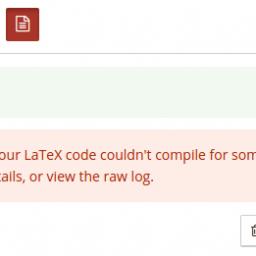
Every day in IT, each one of us walks the fine line between "brilliant" and "appalling." We come across things that make our jaws drop, and we're not sure whether we're amazed or horrified or both. Here's a PHP sample that Brett P. was lucky—or unlucky—enough to discover:
|
 |
by Mark Bowytz on (#2Q13G)
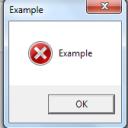
"Maybe it it compiled...maybe it didn't. I guess that I have to find out myself from here on out," wrote, Y. Diomidov.
|
by TJ Mott on (#2PX4J)
Ron used to work for a company which built “smell-o-visionsâ€. These were customized systems running small form factor Windows PCs that operated smell pumps and fans using USB relays timed to a video to give a so-called “4D Experience.†Their product was gimmicky, and thus absolutely loved by marketing groups.One such marketing group, whose client was a branch of the military, worked with them to create a gimmick to help with recruiting. A smell-o-vision was installed on a trailer and towed around the country, used to convince teenagers to join the service by making them smell fresh-squeezed orange juice while watching a seizure-inducing video with guns. The trailer was staffed by grunts, and these guys cycled through so frequently that they received little or no training on the system.“Hey Ron,†Sam, his boss, told him one day. “The recruiter is having a ton of trouble with their system and I need you to go on-site and take a look.â€Going on-site was the only option. The recruiter’s system was not on the Internet so remote diagnosis was impossible. And so he soon found himself cooking in the hot desert sun on a base in the Southwest, looking at a small LCD screen on a 1U pull-out tray accessible through an access panel in the trailer.“This is what it always does,†said the grunt assigned to work with him. “It always says it’s corrupted and the 4D stuff doesn’t work. Rebooting doesn’t fix it.â€Ron looked at the screen as the outdated Windows XP booted up and watched it flash an error stating “Windows was not properly shut down†before beginning a long filesystem scan and repair and then using System Restore to return to an earlier checkpoint. A checkpoint created before the presentation software was installed…Ron shook his head and started the Help Desk 101 questions. “Do you shut down the system when you’re packing up?â€â€œOh, we just turn the generator off,†the grunt answered. “That shuts everything down.â€Ron mentally facepalmed. “You need to properly shut down the system before killing power or this will happen again.†He went inside the trailer and showed them a power button on the control panel. The button was just wired to the power switch header on the PC’s motherboard and acted exactly like any computer case’s power button. Pressing it briefly tells the operating system to shut itself down. “Just press this button and it will shut itself down in a minute or two.â€â€œOkay, that’s simple enough,†the grunt said.Then Ron spent the day re-installing and configuring their system by downloading all the software over his phone’s mobile hotspot to his laptop, then transferring it via USB stick. Eventually he had it back up and running. He made sure to stress how important it was to shut down the system, and on a whim left them a DVD with all the software so he could talk someone through the process over the phone if it happened again.He returned home. And two weeks later, it happened again. He spent three days on the phone talking to a different grunt and walking him through restoring the system. Again he emphasized the importance of shutting down the system with the power button before killing power, but this grunt explained he did that. Ron was confused, but finished the support call.Just a few days later, they called again. He talked to yet another grunt, asked them how shutdown was handled, and he explained he pressed the button until it shut down. His boss decided to send Ron on-site again, and he repaired the system. It was much faster this time since he had a DVD with everything he needed on it, only taking most of a morning. When he was done, he tested the power button. It shut down the system properly.“Show me how you get ready for a presentation,†he asked. “From setup once you’re on-site, to shutdown.â€The pair of grunts assigned to him–two more he’d never worked with before–spent an hour walking through the process. When they got to the end, Ron reminded him to shut down the system.And the grunt did so. By pressing and holding the power button for about five seconds. Which killed power to the PC without properly shutting down the operating system.He mentally facepalmed again. “No, you can’t press and hold. Just tap the button. It will eventually shut down.†He was getting fast at restoring the system and spent that afternoon correcting it all. This time he took a System Restore snapshot once everything was in place, and taped a hand-written note on the control panel saying “DO NOT HOLD THIS BUTTON TO TURN OFF THE MACHINE. DO NOT SHUT OFF THE GENERATOR WITHOUT FIRST TURNING THE SYSTEM OFF PROPERLY.â€He returned home. And a couple weeks later, they called again. He was unable to fix it over the phone and was sent on-site yet again. This time the filesystem was too corrupted to repair and he had to set everything up from scratch. Upon querying the new grunts he discovered they ignored the note and were still holding the power button to kill the system.This continued for a couple more months. The client refused to shut down the system properly and was constantly causing severe filesystem corruption or even killing hard disks. Each time the client called, getting angrier and angrier. “It says there is no OS! I thought you fixed this bug!!†Each time the problems were caused by operator error.During a meeting with his boss Sam, Ron explained all the issues and how much of his time it was taking, and while brainstorming a solution Ron pitched a new idea. “What if we modify the custom power button? Alter it to only send a pulse, instead of a constant closed signal, so it’s impossible to hold it down?â€â€œFigure it out and do it,†Sam ordered. “These guys are idiots and won’t do things right. They’re killing us on support time, we have to fix this or fire the client. How hard is it to shut this thing down properly?â€So, being a software engineer, Ron devised a clever solution based on an Arduino that sampled the power button’s state and sent pulses to the motherboard’s power button header. It passed all his testing and he went on-site to install it. And finally the support calls ceased completely. This unit was the only one that received the update since none of their other clients had issues with operator error.With the issue solved, Ron decided to take some badly-needed vacation to attend a family reunion in North Carolina and tried to stay off the grid. Meanwhile, Sam took a demo unit to an expo in London so visitors could smell what it was like to go skiiing.During his vacation, Ron received a phone call from Sam in the middle of the night. Being on vacation and trying to stay offline, he ignored it. But the phone rang in quick succession several more times and he finally answered.“Ron! Sorry to wake you, but our demo unit quit working and I need your help!â€Ron grunted. “It’s one AM here…â€â€œI know but I need to get this back up before the conference starts this morning!â€â€œOkay,†he said with a sigh. “What’s it doing?â€Sam proceeded to describe a series of error screens over the phone. It stated that “Windows was not shut down properly,†followed by a long filesystem scan, followed by an error that critical system files were corrupted and Windows could not boot.Ron facepalmed for real this time. [Advertisement] Universal Package Manager - ProGet easily integrates with your favorite Continuous Integration and Build Tools, acting as the central hub to all your essential components. Learn more today!
 |
by Remy Porter on (#2PRZD)
Last week, I shared some code that, while imperfect, wasn’t that bad. I then issued a challenge: make it worse. Or better, if you really want. As many comments noted: one case covers only the first iteration of the loop, and one case only covers the last iteration of the loop. You could easily pull those out of the loop, and not need a for-case at all. Others noticed that this pattern looked like odd slices out of an identity matrix.With that in mind, we got a few numpy, Matlab, or MatrixUtils based solutions generally were the “best†solutions to the problem: generate an identity matrix and take slices out of it. This is reasonable and fine. It makes perfect sense. Let’s see if we can avoid making sense.I’ll start with Abner Qian’s Ruby solution.
|
 |
by Jane Bailey on (#2PMQG)
She'd resisted the call for years. As a senior developer, Makoto knew how the story ended: one day, she'd be drafted into the ranks of the manager, forswearing her true love webdev. She knew she'd eventually succumb, but she'd expected to hold out for a few years before she had to decide if she were willing to change jobs to avoid management.But when her boss was sacked unexpectedly, mere weeks after the most senior dev quit, she looked around and realized she was holding the short straw. She was the most senior. Even if she didn't put in for the job, she'd be drafted into acting as manager while they filled the position.This is the story of her first day on the job.Makoto spent the weekend pulling together a document for their external contractors, who'd been plaguing the old boss with questions night and day— in Spanish, no less. Makoto made sure to document as clearly as she could, but the docs had to be in English; she'd taken Japanese in high school for an easy A. She sent it over first thing Monday morning, hoping to have bought herself a couple of days to wrap up her own projects before the deluge began in earnest.It seemed at first to be working, but perhaps it just took time for them to translate the change announcement for the team. Just before noon, she received an instant message.Well, I can just point them to the right page and go to lunch anyway, she thought, bracing herself.Emilio: I am having error in application.
|
 |
by Remy Porter on (#2PGM1)
There’s a lot of debate about how much a developer should rely on comments. Clear code should, well, be clear, and thus not need comments. On the other hand, code that’s clear the minute you write it might not be as clear six months later when you forget what it was for. On the other, other hand, sometimes a crime has been committed and we need the comments for a confession.Austin S confesses his crime.
|
 |
by Mark Bowytz on (#2P6ZV)
"What do you think the buttons do? If you thought the dialog was trying to help you log in or give an opportunity to send them an e-mail, instant message, or tweet pointing out how the buttons don't do anything, you might be mistaken," writes Alex M., "
|
 |
by Jane Bailey on (#2P302)
As many of you know, outside of being a writer, I also work on open-source projects. The most famous of these is Sockbot, a chatbot platform that interfaces with various forum and message clients. If you're reading this, my boss didn't object to pointing out that my work has never made this particular mistake—but maybe we'd be more famous if we had.This particular chatbot was designed for internal use. The company, like many others, had moved to Slack as an IM program for their development teams. Like every other team that found themselves with a slack, the developers quickly set about programming bots to interact with the platform and assist with common tasks like linking to an issue in the company Jira, pushing out a docker container to the QA environment, and ordering lunch.Today's submitter, Suzie, wanted to add Google search to her local bot, Alabaster. Often, when people started talking about something, they'd grab the first link off Google and dump it into the chat for context. This way, Alabaster could do that for them. Sure, it wasn't the most useful thing in the world, but it was simple and fun, and really, isn't that why we program in the first place?Of course, Google puts a rate limit of 100 queries per day on their searching, and you need an API key. Bing, on the other hand, had a much higher limit at the time of 5,000 queries a month, and was much easier to integrate with. So Suzie made the executive decision to settle for Bing and eat the gentle razzing she'd get in response.If you've never used a chatbot before, there's two ways to design them. The harder but much-nicer-to-use way is to design a natural language processor that can tell when you're talking to the bot and respond accordingly. The easier and thus far more common way is to have a trigger word and a terse command syntax, like !ban user to ban a user from the chat room. Command words are typically prefixed with a bit of punctuation so they can't accidentally be used to start a sentence, too. In the example I gave, the ! informs the bot that you're talking to it, and ban is the command, given the argument user to the command handler.Alabaster was using !! as his trigger, so Suzie settled on !!bing as the bot command to start a search, passing in the rest of the line. Since she wasn't using Sockbot, she had to handle the line parsing herself. She went the easy way and replaced the first instance of the word "Bing" with empty space before handing the rest of the line to the Bing API.Or ... she tried to. In reality, she wrote var searchText = message.TargetedText.ToLower().ReplaceFirst("big ", "").Trim();, missing the all-important "n" in "bing".This wouldn't usually be a big deal. If you start your Google search phrase with the word "google", it's usually ignored while Google searches for the rest of the phrase. Bing, however, is also part of several people's names, such as Bing Crosby, Chandler Bing ... or porn star Carmella Bing, the most searched of the three. Somehow, Suzie had also allowed the searches access to NSFW results. Every time Alabaster was asked to search, it came back with X-rated results about the porn star.Suzie scrapped the module and started over. This time, she decided Google's rate limit was probably just fine ... just fine indeed. [Advertisement] Application Release Automation for DevOps – integrating with best of breed development tools. Free for teams with up to 5 users. Download and learn more today!
|
 |
by Remy Porter on (#2NZ1Z)
So, fun fact about myself: I didn’t know what the For-Case anti-pattern was until relatively recently, when there were a spate of articles condemning it as an anti-pattern. I’m sure I’ve probably used it, at some point, but I never knew it by name. It’s thought of as a textbook antipattern that generally implies a misunderstanding of for loop, case statements, the problem being solved, or some combination of all three. That said, there are certain problems that might be more clear to solve by using the For-Case. Like GOTO, it might be harmful, but its actual evil exceeds its reputation.John A had a problem, and most unfortunately for him, this problem involved VBA macros embedded in an Excel spreadsheet. He needed to generate four arrays, that fall into this pattern:
|
 |
by Remy Porter on (#2NVQF)
|
 |
by Remy Porter on (#2NV4N)
It was a particularly irritating Monday morning, when Travis got a frantic text from his boss. The sun was shining, the birds were nattering, and everyone was greeting him with a smile; it was like everyone in the world had their coffee, but Travis overslept and was going to have to satisfy himself with whatever sludge he could scrape out of the office coffee maker. He had just crossed the threshold when the text arrived:
|
 |
by Remy Porter on (#2NQBR)
If you want to send emails from a Java program, you might be tempted to use the javax.mail package, which contains objects for doing exactly that. It’s a relatively straightforward API, and while it’s a bit verbose, that’s hardly unusual for Java. You just wrap it up in a convenience function based on how you need to call it, and reuse that, right?Well, PHP, an obviously superior language, already did that work. There’s a built-in mail function, which sends emails. It uses your php.ini file to figure out what SMTP service to use, making the parameters to the function more “obviousâ€.Chris had a co-worker that really loved the… elegance… of PHP’s solution to this problem, and thus, when they needed to send emails from Java, they did it this way:
|
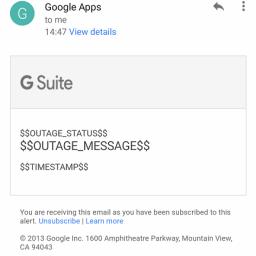 |
by Mark Bowytz on (#2NE41)
"When Google's having an outage, and it's also affecting their outage notification service, things are NOT going well" writes Nathan.
|
 |
by Remy Porter on (#2NACR)
Have you ever fallen asleep on your keyboard? Aside from the awkward face-prints it leaves behind, did you notice yourself programming in your sleep? I suspect that Chris’s co-worker does sleep-program. At least, that’s the only explanation for the 7,088 line code-sample I’m about to show you. Don’t scroll too fast- there’s actual code mixed into the middle of this. And yes, I’m including all of the code.Which is less than you’d think, from the line count.
|
by snoofle on (#2N6DX)
 |
by Remy Porter on (#2N2B9)
Pearl’s employer couldn’t find an off-the-shelf product that handled their call-center needs, so they developed one in house. One department didn’t want to use that front-end, so they developed a different one in house, but it still used the same backend… mostly. Another group did the same thing, adding some fields and extending the database. And then another. Then there was an organizational restructuring, and suddenly the call-center reps found themselves in the annoying position of needing to do double- or sometimes triple-entry, in order to get all the right columns and fields filled out based on the current business rules.Now this is a textbook example of where one might want to engage in some business process improvement: identify the actual needs of the organization, and implement software suited to those needs (chucking out any legacy kruft that you don’t need). Doing this, of course, takes some work, it takes some analysis, and it takes an organization willing and ready to make changes.Pearl’s organization was not ready and willing to make changes. Instead, one of the PHBs had recently read an article on “robotic process automationâ€, which is a fancy way of saying, “we’re gonna screen-scrape using a fancy drag-n-drop workflow tool.†Instead of spending time and money training the in-house developers to use the tool, the company could outsource it to a much cheaper team that already had experience.Now, one-size-fits-all drag-n-drop scripting usually fails on the difficult edge cases, and Pearl’s company had lots of difficult edge cases. No problem, the offshore team could just write some C# scripts to do the job, and call them from the workflow tool.This is the script CheckFallingDate.cs which does… something.
|
 |
by Jane Bailey on (#2MYP2)
It was early in Seth's tenure at PicoServices Inc. when he first heard about Joe."Oh, man," he was told by a coworker he'd recognized as having a good head on her shoulders. "I can't wait until you end up at a Joe review.""Joe? Why's that?" he asked, tilting his head."Nope, no way. You get to experience Joe the hard way."Over the coming week, Seth was pretty sure he'd caught people taking bets for something to do with the coming code review, but he wasn't sure why. Joe had seemed like a reasonable fellow when they'd reviewed Beth's code together, and he'd had a few useful pointers for Seth about how to talk to one of their project managers. What could be so bad?When he got to the conference room where the team had gathered to review Joe's new code, Beth beckoned him over to sit by her, right at the base of the U-shaped table where he had a prime view of the projector. As Joe got his laptop plugged in, most of the room seemed to be watching Seth's face with varying degrees of subtlety.Oh ... kay ... Seth thought, bracing himself for some weird hazing ritual.Then the projector flickered to life, and he settled in to read the function.
|
by Mark Bowytz on (#2MMK1)
"If you want to sneak in an ad that doesn't necessarily belong in Kongregate, I guess a little creative spelling is one way to do it," wrote Ben J.
by Erik Gern on (#2MGGP)
WT Durham had never met Bruce, former sales executive and new COO of Prepackaged Pixels, before he paid a visit to WT’s department. They were responsible for maintaining the licensing API for the company’s toolkit bundle, which included their prized platform-agnostic GUI. The bundle was used for internal projects as well as for third-party licensing, and customers often bought the entire bundle just to use the GUI. Bruce wasn’t too happy about that.“We’ve conducted several customer surveys,†Bruce said. “Two-thirds of our customer base only want the GUI toolkit, not the rest of our bundle.â€â€œIsn’t that a good thing?†WT replied. “We get a big markup on selling our toolkits as a bundle.â€â€œWe could capture more of the market if we sell the GUI toolkit separately,†Bruce responded. “We need the ability to license just the GUI.â€â€œWe’ll need to refactor our API.†WT did some mental calculations. “It’ll take our team six months.â€â€œAll twelve of you working for six months?!†Bruce shouted. “Just to make the installer work with one toolkit? That thing is 150MB! I’ll bet the installer would be one-tenth of that size with just the GUI toolkit.†Bruce made it clear that single-toolkit licensing – and decreasing the size of the installer – would be their priorities.Stovepipe SolutionWT wasn’t sure where Bruce, who had no programming experience, had gotten that information about the install size, but had a suspicion it was the head of the GUI toolkit team.“He called me first.†Mindy, senior developer for the GUI toolkit, welcomed WT into her office. “Probably right after he got promoted.â€â€œYou told him the installer size was 150MB?â€â€œI was making nice. Everyone complains about the size of the installer.â€WT sighed. “We inherited the installer codebase from a contractor almost ten years ago and built the licensing API on top of it. I told Bruce it would take six months to refactor for single-toolkit licensing, but who knows how long it would take to figure the base installer code out.â€â€œMaybe you can just trim it down?†Mindy suggested. “Fork the installer, tear out anything not related to the GUI, and stovepipe the licensing code for now. That would take less than six months, right?â€Redundant RedundanciesWT convinced the rest of his team to give the stovepipe solution a try. At worst, it would be a month wasted. At best, it would save them months of development time, allowing them to refactor the licensing code – and the underlying installer – properly later on.While every part of the installer was audited, they would analyze their installation statistics, seeing exactly what environments they needed (and which they could chuck). If a particular environment fell below 5% of their installation base, they’d throw it out.As the audit progressed, it became very apparent just why their installer was 150MB. Binaries were distributed in both 32- and 64-bit varieties, and each API namespace had its own binary. There were also optimized binaries for three different compilers. Each of these were duplicated again for debug and release versions. In all, 24 binaries per library were shipped in the installer.And the installation stats? Nearly every installation was for the 64-bit GUI toolkit, using two of their three supported compilers. Out of 24 copies of each library, they needed only two.Crash DietBruce’s demeanor changed when he heard that the licensing team could deliver a GUI-only installer in a month. “I knew it wasn’t that hard!†he said, not knowing at all how hard it was.Unfortunately, sales of the overpriced bundle – which included the GUI as well as their other toolkits – fell, as everyone bought the discounted GUI-only installer instead. Without their marked-up product sales, Prepackaged Pixels faced their first quarter without a profit. Bruce weathered the storm, but WT and others fell victim to layoffs.Several years later, WT bought a license for Prepackaged Pixel’s toolkit bundle for a freelance project. The company no longer sold GUI-only licenses, so WT had to download the entire bundle – all 150MB of it. Prepackaged Pixels had kept their business model intact, but hadn’t been able to de-bloat their installer.[Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
 |
by Remy Porter on (#2MCG2)
I recently have needed to write some systems that do analysis on a stream of samples. The target stream of the analysis process was stored in a variable targetOfAnal, because obviously, that’s more efficient to type than targetOfAnalysis. I of course needed an analProcess and analComplete flag, and yes, my inner 13-year old was snickering the entire time.James’s co-worker decided to demonstrate that immature dirty jokes should only be taken so far. James heard him cursing up a storm, and thus offered to help debug whatever the problem was. You could say this code is hitting the “dirty variable names†button a bit too hard. I present it here without modification, because honestly, there is no way to censor this code and have it convey its full meaning. Ready your alt-tab before the boss comes by:
|
 |
by Charles Robinson on (#2M8E6)
Having survived the scourge of Jack's automated testing debacle, Rita thought she could handle anything. Since that time, Rita had Operations burn/kill/destroy all the JCKRKS servers and set up new ones that she had full control over. Rita felt well-prepared for a future where nothing that bad could happen again. But sometimes those who only look forward are unprepared for the return of a long-forgotten relic.In a different IVR-enabled part of their health insurance system, customers could call in to hear information about their health benefits. These benefits, as is par for anything with health insurance, were governed by a very complex set of rules, contracts, overrides, and addendums. Depending on the caller's employer, benefit administrator, subscriber level, eye color, astrological sign and feng shui positioning, their very specific set of benefit information would be read back to them.To house this complex set of business rules, the organization depended on ILOG to keep things in order. It did the job but when it came time to tweak said rules, customers had to file a formal change request and wait weeks to see their change implemented. Customers complained about the process enough that Gregor, bringer of Jack, had the bright idea to give them a way to make rule changes on the fly themselves."It's quite simple, Rita," he began to explain with an arrogant tone. "It's taking too long for our customers to get their changes and it takes too much of our time to implement them. We need to create a web-based way for them to alter their business rules and I think you're just the girl to make it happen!""Gregor, I agree that we could do better with this, but are you sure we want our end-users messing around with complicated settings? Things could get ugly in a hurry," Rita expressed great concern."Point taken, but I still think this is a brilliant way to make everyone happy and more productive! Plus we can deprecate that expensive ILOG system and just store everything in a database! Get to work."So began a large unplanned, unbudgeted project to get the web interface built with a SQL backend while exporting all the data from ILOG to a massive Excel spreadsheet. It drove Rita to her wit's end but she started to see the light at the end of the tunnel. They were now prepared for a round of beta testing by HealthLords, their biggest client (see: biggest complainer).The HealthLords were excited to get started so they could brag about being the first insurer to set up their own business rules. They logged in to Rita's slick web interface and began to manipulate stuff. As they dug through their extensive set of rules, they came across one that was foreign to them - "PAUL TEST DO NOT DELETE". They opened it up to find the shocking description of "This is just an internal test. Those whiny HealthLord idiots will never see this once ILOG is implemented."Almost immediately, Rita received an angry call from a big whig at HealthLords. Caught off guard, she was only able to offer a token apology and promise to look in to it. It had never been there before, so it was definitely a mystery to solve.She dug in to the IVR platform that was still being used before and after the days of ILOG. After many rounds of tracing the code, she found the rule embedded deep in a dusty corner of the code in a class that shouldn't have processed benefit addenda at all. There stood a comment on the offending rule, "// remove this if we decides [sic] to pay for ILOG ~ Paul".Paul hadn't been with the company for several years and had quit just before the ILOG system was implemented. But that didn't mean Rita couldn't curse his name on this day. ILOG had been covering up his test rule forever and now that it was out of the picture, it showed up again during HealthLords' beta testing. It took Gregor escalating to his bosses' bosses' boss just to keep HealthLords from backing out of their contract. [Advertisement] Universal Package Manager – store all your Maven, NuGet, Chocolatey, npm, Bower, TFS, TeamCity, Jenkins packages in one central location. Learn more today!
|
 |
by Remy Porter on (#2M4P4)
UUIDs, aka GUIDs are, well… unique. Unique identifiers. It’s right there in the name.Active Directory needs to identify things. Thus, it uses GUIDs. “Omni’s†co-worker got this far, but then ran into a problem. If you print a GUID from AD, it looks like this: “35918bc9196d40ea9779889d79b753f0â€, but if you print it from C#, it looks like this: “35918bc9–196d–40ea–9779–889d79b753f0â€. Whatever is a programmer to do when dealing with these radically incompotible formats?
|
by Mark Bowytz on (#2KV4Y)
"I'd say that this brings new meaning to what a 'core dump' really is," Paul N. writes.
 |
by Remy Porter on (#2KQ2P)
Tony Hoare has called null references his “billion dollar mistakeâ€. Dealing with nulls and their consequences have created a large number of bugs, and eaten a lot of developer time. It’s certainly bad enough when you understand nulls and why they exist, but Benjamin Soddy inherited code from someone who absolutely didn’t.First, there’s our new type, the ByteBool:
|
by Remy Porter on (#2KJVM)
In the Before Times, the Ancients would gather in well-sheltered caverns, gather to themselves foods blessed by the gods, drink strange, unnaturally colored concoctions, and perform the Rite of the LAN Party.In the era when the Internet was accessed by modem, to have any hope of playing a game with usable latency, you had to get all the players in the same place. This meant packing up your desktop in a car, driving to your friend’s house, and setting up your computer on whatever horizontal surface hadn’t already been claimed by another guest.
 |
by Ellis Morning on (#2KETK)
|
 |
by Jane Bailey on (#2KBBN)
Monday morning, 10:00AM. As per usual, today's protagonist, Merv, got some coffee and settled in for his usual Monday morning routine of checking Facebook and trying to drag his brain into some semblance of gear. As he waited, the least interesting conversation ever floated to his ears from the hallway:"It's like, yak butter, I guess? I put it in my coffee, it's supposed to do wonders."
|
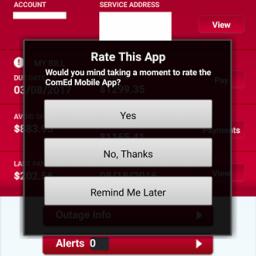 |
by Mark Bowytz on (#2K2T4)
"Since clicking 'Yes, I mind', took me to the review page, I left a one star review," writes Pascal.
|
 |
by snoofle on (#2JZ96)
We've all been approached for jobs where the job description was merely an endless list of buzzwords across disciplines, and there was no real way to figure out what was actually the top couple of relevant skills. The head hunter is usually of no help as they're rarely tech-savvy enough to understand what the buzzwords mean. The phone screen is often misleading as they always say that one or two skills are the important ones, and then reject candidates because they don't have expertise in some ancillary skill.Teddy applied for a position at a firm that started out as a telco but morphed into a business service provider. The job was advertised as looking for people with at least 15-20 years of experience in designing complex systems, and Java programming. The phone screen confirmed the advert and claims of the head hunter. "This is a really great opportunity," the head hunter proclaimed.Then it was time for the interview. The interview was the sort where you meet with the manager, a peer of the manager, and several senior members of the team, repeating your work history for each one.There was a coding exercise to see if you could convert an int to a Roman numeral and vice versa.Each person asked some simplistic architectural design type questions...
|
 |
by Remy Porter on (#2JVAW)
Cédric runs the backend for a video streaming service. Since video streaming, even in modern HTML5, is still a bit of a mess, they have to be able to provide many different stream formats. So, for example, the JSON data might look like this:
|
 |
by Ellis Morning on (#2JQGC)
In the mid-90s, Darren landed his first corporate job at a company that sold IT systems to insurance brokers. Their software ran on servers about the size of small chest freezers—outdated by the 70s, let alone the 90s. Every month, they'd push out software fixes by sending each customer between 3 and 15 numbered floppy disks. The customers would have to insert the first disk, type UPDATE into the console, and wait for "Insert Disk Number X" prompts to appear on screen.It wasn't slick, but it worked. The firm even offered a recycling service for the hundreds of disks that eventually built up at customer sites.While working there, Darren became unfortunately well acquainted with one particular insurance broker, Mr. Lasco. The man refused all offers of training ("Too expensive!") and paid support ("You don't know enough!"), and was too good to read instructions, but could always be counted on to tie up some poor tech support rep's phone every time a new update went out. He never let them charge the call against his company's account, or even thanked anybody for the help. When told about it, management just shrugged their shoulders. Mr. Lasco's firm did have a big contract with them, after all.Early one Monday morning, Darren answered his phone, only to receive an ear-splitting tirade. As Mr. Lasco ranted, Darren held in a sigh and used the time to start filing a support ticket."What's the nature of your problem, sir?" he asked during the gap in which Mr. Lasco paused to breathe."I—it's—your damn update won't work! Again!" Mr. Lasco sputtered. "My machine is full!"Darren frowned. That wasn't an error message that the update process would ever throw. "'Full?' Hmm, maybe one of the server's hard drives is out of disk space? Maybe you need to—""No, you fool, it's full! It's FULL!" Mr. Lasco snapped. "I KNEW this would happen eventually! Do you know how much money I'm losing right now with this thing down? I want one of your people to come out here and fix this immediately!"The demand prompted an eyeroll from Darren, who already knew Mr. Lasco would never pay for a consultant's time. Still, this was a perfect way to get him off the phone. "Why don't I forward you to your sales rep?"To Darren's amazement—and pity—a software engineer was dispatched within the hour to drive several hundred miles to Mr. Lasco's site, with instructions to call Darren with updates.By late afternoon, the call came. The engineer was laughing so hard, he couldn't talk."Is everything OK?" prompted Darren."Wait'll you hear this." The engineer struggled to breathe. "There's a gap in the server casing. All this time, Lasco's been inserting update disks into the server, and couldn't force any more in. I popped the case open, and swear to God, there must be a few hundred disks crammed in there, easy. Years of updates!"Darren joined in the mirth, but it was short-lived. The poor engineer had to spend 7 hours onsite carefully extracting floppy disks wedged between drives and memory cards, sorting them, then applying the updates in order.The one silver lining to the whole affair was that Mr. Lasco never called them again.[Advertisement] Manage IT infrastructure as code across all environments with Puppet. Puppet Enterprise now offers more control and insight, with role-based access control, activity logging and all-new Puppet Apps. Start your free trial today!
|
 |
by Remy Porter on (#2JKYD)
In the Star Trek episode, “A Piece of the Actionâ€, Kirk and his crew travel to Sigma Iotia II, a planet last visited before the Prime Directive of non-interference existed. Well, they left behind a book, Chicago Mobs of the Twenties, which the Iotians took as a holy guide, to be imitated and followed even if they didn’t quite understand it, a sort of sci-fi cargo-cult. Cue the crew of the Enterprise being threatened with Tommy Guns and guys doing bad Al Capone impressions.Michael’s co-worker may have fallen into a similar trap. An advanced developer came to him, and gave him a rule: in PHP, since variables may be used without being declared, it’s entirely possible to have an unset variable. Thus, it’s a good practice to check and see if the variable is set before you use it. Normally, we use this to check if, for example, the submitted form contains certain fields.Like Bela Okmyx, the “Boss†of Sigma Iotia II, this developer may have read the rules, but they certainly didn’t understand them.
|
 |
by Mark Bowytz on (#2JDA1)
"I too have always felt that discount codes are a great way to express sympathy," writes Shawn A.
|
 |
by Remy Porter on (#2JAFG)
Microsoft’s C# has become an extremely popular language for “enterprise†development, and it’s sobering to think that: yes, this language has been around for 15 years at this point. That’s long enough for the language to have grown from a “sort of Java with reliability, productivity and security deleted.†(James Gosling, one of the creators of Java) to “sort of Java, but with generics and lambdas actually implemented in a useful way, and not completely broken by designâ€.15 years is also more than enough time for a project to grow out of control, turning into a sprawling mass of tentacles with mouths on the ends, thrashing about looking for a programmer’s brain to absorb. Viginia N is currently locked in a struggle for sanity against one such project.Some of the code looks like this:
|
 |
by snoofle on (#2J7KD)
A long, long time ago when C was all the rage and C++ was just coming into its own, many people that were running applications on Unix boxes used the X-Windowing system created by MIT to build their GUI applications. This was the GUI equivalent of programming in assembly; it worked, but was cumbersome and hard to do. Shortly thereafter, the Xt-Intrinsics library was created as a wrapper, which provided higher level entities that were easier to work with. Shortly after that, several higher level toolkits that were even easier to use were created. Among these was Motif, created by DEC, HP, etc.While these higher level libraries were easier to use than raw X-lib, they were not without their problems.Sam was a senior developer at Military Widgets, Inc. His responsibilities included the usual architectural/development duties on his project. One day, Pat, Sam's boss, asked him to stay late. "Taylor has a bug that he just can't crack," Pat explained. "I want someone with a little more experience to give him a hand."It seems that after making some changes to their Motif GUI, the application started throwing stack dumps on every transaction. As a result, every transaction was rolling back as failed. Taylor insisted that his code was correct and that it was not the cause of the problem. To this end, Pat asked Sam to stay late one afternoon and take a look at it.After some company-sponsored pizza, Pat had Taylor hand Sam a stack trace. In the middle of it was a call to:
|
 |
by Remy Porter on (#2J3QQ)
There’s plenty of bad code that makes you ask, “what were they thinking?†There’s a whole bunch of code we get, however, that doesn’t even raise that question- the programmer responsible simply wasn’t thinking. Today, let’s examine a few “programmer brain-fartsâ€. We turn our attention first, to Jim C.While reviewing some unit tests, he found this line:
|
by Lorne Kates on (#2J06S)
Radio WTF Presents!Jump to transcriptWelcome back to Radio WTF. This week, we visit a two kilometer wide mushroom in space, and find out WTF happens when unexpected guests arrive...Soundcloud Links:Radio WTF: Space for GuestsDirect Download:SpaceForGuests.mp3Starring (in order of appearance)Jane Bailey... as Commander Josephine Garneau
by Mark Bowytz on (#2HPQC)
"I have a feeling that VS Code is trying to tell me that the object class provides functionality common to all JavaScript objects," writes Eric.
by Jane Bailey on (#2HJWA)
Hikari had just left Apps R' Us when our submitter, Steve, was asked by the CEO to review some of his code. Now, Steve wasn't on the same project as Hikari, but he had a reputation for being thorough and concise, while Hikari had a reputation for being fast but sloppy. Apps R' Us was a smallish shop, so Steve was a good pick for taking over the project despite barely knowing the requirements.Hikari was working on an augmented reality game for a very specific problem domain. In this use case, GPS was going to be unreliable. Instead, they needed to focus on the compass heading and rough location most times, at most correcting a little from GPS data. Steve skimmed through the code, looking for the overall structure before he dove into the fine details, but the following comment stopped him in his tracks:
by Remy Porter on (#2HETF)
Usul is taking a college course on Java programming, and it’s doing an excellent job preparing him for the real world. Already, he’s been forced to cope with someone who knows one true fact and has run off to apply it in the dumbest way possible. This would be his professor.Our true fact is this: A Java PreparedStament object, used for running database queries, should be closed after use. This returns its connection to the pool and frees any resources the statement was using. You should do this, and you should do it as soon as you’re done with your connection.Now, putting a call to stmt.close() in every finally block was just too much for Professor McCloseypants to deal with. So he provided this “convenience†object to deal with that problem.It’s a lot of code, so we’re going to do this in pieces. First, let’s look at the declaration:
by TJ Mott on (#2HAS3)
David was recently hired on to head the company’s development team. This was a brand-new position; previously, William, the company’s IT Manager managed the developers directly in addition to his other duties.While getting his workstation set up, he was unable to install the FileZilla FTP client. It was completely blocked via domain policy. Finding this very strange, David talked to the IT Manager and hoped there was a legitimate reason.“FTP is a big security risk,†William explained. “We got hacked through FTP once so I firewalled it by blocking FileZilla installation with Group Policy.†David began to suspect that things at the company were not quite right.“Um, Group Policy isn’t a firewall,†David tried to explain. “And blocking an FTP client installer is unlikely to have an effect on network security.â€William clearly didn’t understand and doubled down on his incorrect ideas. “Trust me, it works,†he said. David soon gave up and simply installed a different FTP client–which worked just fine despite FTP being “firewalled.â€Later, while familiarizing himself with the business’s core applications, David decided to examine the company’s main database server. “It’s set up with RAID 10 for the best performance,†William explained. RAID 10, sometimes called RAID 1+0, mirrors all data into two arrays for fault tolerance, and then each array is striped onto additional disks to greatly improve read/write performance. It’s one of the fastest RAID configurations and a great fit for database servers.But David ran a disk benchmark and was not convinced. “That disk I/O is way too low for RAID 10,†he explained. “Can you show me the configuration?â€â€œOf course,†William replied. “It has to be RAID 10. We ordered it that way.â€They opened the RAID manager for the system, and sure enough the system was not running RAID 10. “Um, this is RAID 5,†David explained. RAID 5 uses three or more disks for striping, but the capacity of one disk is lost for storing parity data which allows the array’s data to survive a single-disk failure. Due to the required parity calculations, RAID 5 writes are not nearly as fast as RAID 10, which is bad for an I/O bound application such as the company’s main database server.“That can’t be,†William responded. “Oh, I know…Kieran must have changed it!†He called the company’s so-called systems administrator to the room, and David endured the uncomfortable exchange as William hurled wild accusations. “I know we ordered this system with RAID 10! Why did you change it?â€â€œI just unboxed it and racked it,†Kieran responded. “Whatever RAID level it has is what it was shipped with.â€â€œThat can’t be true! You tampered with it!â€Kieran rolled his eyes and turned to leave. “I have real work to do elsewhere,†he rudely explained as he excused himself from the conversation. Later on, he sent an email to both David and William which contained the original Purchase Order for the server. The PO clearly showed that William had specifically requested RAID 5 for the server.David found himself wondering if management was aware of William’s behavior and general incompetence, but tried to avoid making waves during training. But the final straw came when he set about installing several of the company’s internal applications and was unable to find any installers on his own. Once again he went to talk to William.“Oh, we don’t install any of our applications. That’s too slow!†he explained. “Instead, look at the database server. It has a shared folder called ‘APPS’, and just map that as a network drive and run everything from there.â€Once again, David found himself doubting the IT Manager’s wisdom. “Doesn’t it hurt our database performance to have the entire company mapping a network drive to the same RAID array as the databases?†he asked.“Oh no,†he replied. “It actually makes it faster. The apps can talk to the database much faster if they’re running from the same server!â€David was stunned by William’s poor understanding of how network-mapped file systems actually work. “That might be true if it was a terminal server…but the applications still run locally on the end user PCs. The files just happen to be stored elsewhere.â€â€œWhat do you know, you’re still the new guy! We’ve had this procedure in place for years now, and for good reason!â€Despite being a newbie, David decided to approach management about the ineptness he’d discovered, and explained that William was rude, incompetent, and had no business working in IT. To his surprise, management conducted a brief investigation and agreed with him! Shortly afterwards, William was let go.The new IT manager was shocked at the company’s infrastructure and quickly made a range of improvements. This included installing a proper Storage Area Network which greatly improved the database server’s performance; a new storage pool for mapped drives which was on separate disks than databases; and a real hardware firewall which, among other things, actually blocked incoming FTP connections from the Internet.David then forwarded his story on to us at The Daily WTF as a reminder that sometimes things actually do turn out okay in the vast WTF-land that is the IT industry. [Advertisement] Easily create complex server configurations and orchestrations using both the intuitive, drag-and-drop editor and the text/script editor. Find out more and download today!