 |
by Simon Sharwood on (#5KYMK)
No fixes yet for Windows 10 version 1607, Windows Server 2016, or Windows Server 2012 Microsoft has issued out-of-band patches for the PrintNightmare print spooler bug that allows lets remote Windows users execute code as system on your domain controller.…
|
The Register
| Link | https://www.theregister.com/ |
| Feed | http://www.theregister.co.uk/headlines.atom |
| Copyright | Copyright © 2026, Situation Publishing |
| Updated | 2026-03-10 08:16 |
 |
by Simon Sharwood on (#5KYHR)
CEO comes out swinging, says 'people make the story and make the impact of this larger than what it is' Kaseya’s attempt to recover its SaaS services has failed, and its CEO has attempted to play down the significance of the incident that has seen its VSA services offline since July 2nd and over 1,000 ransomware infections.…
|
 |
by Simon Sharwood on (#5KYH5)
NetWire malware used to deliver incriminating letters into obscure directories users could not see Evidence used to charge an Indian man with plotting to assassinate India’s Prime Minister and inciting violence at a 2018 protest was planted on his laptop, according to US digital forensics consultancy Arsenal Computing.…
|
 |
by Iain Thomson on (#5KYGD)
I've got a brand new combine harvester an' I'll give you the firmware update key President Joe Biden is expected this week to sign an executive order directing the formation of rules that ensure Americans have the right to repair ... their farming equipment, at least.…
|
 |
by Thomas Claburn on (#5KYFP)
Documents detail exec worried that failure to transfer some laid-off workers 'will blow a hole in our rhetoric' An IBM age discrimination lawsuit filed in Texas last year has become a bit less opaque after The Register found an inadequately redacted court document that discusses plans to present evidence obtained from company emails and documents.…
|
 |
by Thomas Claburn on (#5KYC3)
Could be brute-forced due to design blunders, according to infosec outfit Last year, Kaspersky Password Manager (KPM) users got an alert telling them to update their weaker passwords. Now we've found out why that happened.…
|
 |
by Laura Dobberstein on (#5KYAY)
Boffins in hospital, official goes to work as normal until social media blows up The head of China Aerospace Investment Holdings has been taken into police custody after a video showing two senior scientists being attacked went viral on China's microblogging site Weibo and TenCent's WeChat last week.…
|
 |
by Gareth Corfield on (#5KY98)
Good luck with that, 4 New Square Chambers A barristers' chambers hit by a ransomware attack has responded by getting a court order demanding the criminals do not share stolen data.…
|
 |
by Lindsay Clark on (#5KY7E)
That's fancy talk for sensors, software, and autonomous technologies btw Infor has sold its asset management applications business to Hexagon AB, a Swedish industrial tech biz, in a deal valued at $2.75bn.…
|
 |
by Katyanna Quach on (#5KY5A)
Y'know what, a single-vendor IT mega-deal probably isn't the best idea after all, says US military Updated The Pentagon has killed off the $10bn JEDI IT contract that Amazon, Microsoft, Oracle, and others spent years fighting over.…
|
 |
by David Gordon on (#5KY5B)
Tune in and we'll help you decide when to make the jump Webcast It’s clear that the rapid advance of artificial intelligence will have a profound impact on businesses of all types. So what should you be doing to prepare your organisation to embrace AI?…
|
 |
by Matt Dupuy on (#5KY30)
It's fine: they'll just be used for searching disaster sites, checking structures, spying on people If there is one thing the world doesn't need, more cockroaches would surely be it.…
|
 |
by Tim Anderson on (#5KY10)
Microsoft identifies 'ecosystem challenges' as reason for not supporting its own system Microsoft has suspended its SQL Server on Windows Container beta "with immediate effect."…
|
 |
by Gareth Halfacree on (#5KY11)
Staggered keys, your days are numbered Enthusiasts of radical ergonomics, high-speed coders, and keyboard hipsters have cause to rejoice: the market will soon boast the world's first laptop with an ortholinear keyboard layout, thanks to not one but two aftermarket upgrades.…
|
 |
by Richard Speed on (#5KXYT)
New name needed. How about Impudence? Or maybe Pluck? Contributors disgruntled with the recent direction of cross-platform FOSS audio software Audacity are forking the sound editor to a version that does not have the features or requirements that have upset some in the community.…
|
 |
by Gareth Corfield on (#5KXX8)
And a third of that's going into the lawyers' pockets British Airways has settled the not-quite-a-class-action* lawsuit against it, paying around £32m to make the data breach case in the High Court of England and Wales go away.…
|
 |
GitHub Copilot auto-coder snags emerge, from seemingly spilled secrets to bad code, but some love it
by Tim Anderson on (#5KXX9)
Great wow factor but is it legal? Is it ethical? Is code that can't be trusted any use? Early testers of GitHub's Copilot, which uses AI to assist programmers to write code, have found problems including alleged spilled secrets, bad code, and copyright concerns, though some see huge potential in the tool.…
|
 |
by Lindsay Clark on (#5KXVE)
COVID-hit body implementing multiple interdependent cloud systems to replace on-prem software The UK's Financial Ombudsman Service (FOS) is on the hunt for an IT services partner capable of supporting and developing its new data warehouse and CRM systems in a deal that could be worth up to £22m.…
|
 |
by Gareth Halfacree on (#5KXSG)
Permissively licensed, the processor's second iteration targets 2GHz at 14nm The Institute of Computing Technology at the Chinese Academy of Sciences (ICT CAS) has showcased progress on a fully open-source processor, designed around the RISC-V architecture, which it hopes will offer competition for Arm parts at the performance end of the market.…
|
 |
by Matt Dupuy on (#5KXQQ)
Irradiated boars rampage across the internet, leaving jokes, memes, fan art in their wake It seems that the monstrous irradiated boar-pig hybrids that we featured in an article last week have broken out of their former home in the exclusion zone around the destroyed Fukushima nuclear plant and are now running riot around the internet.…
|
 |
by Matthew Hughes on (#5KXQR)
Bumpy ride of a keyboard - but that's kind of the point Review This reviewer's desk is a temple of the mechanical. I like my keyboards, and I like them clicky and with oodles of tactile feedback. And yet, for the past couple of weeks or so, I've been using a bog-standard scissor-switch keyboard.…
|
 |
by Davey Winder on (#5KXPJ)
Er... let's just ask the experts boffins Feature Do the laws of physics trump mathematical complexity, or is Quantum Key Distribution (QKD) nothing more than 21st-century enterprise encryption snake oil? The number of QKD news headlines that have included unhackable, uncrackable or unbreakable could certainly lead you towards the former conclusion.…
|
 |
by Simon Sharwood on (#5KXN0)
IDC says on-prem clouds like AWS Outposts will grow from from $140M annual sales to $14B Analyst firm IDC has a new abbreviation for your cloudy dictionary: DCIaaS, which stands for Dedicated (Local) Cloud Infrastructure-as-a-Service.…
|
 |
by Simon Sharwood on (#5KXKR)
Straight-up copyright complaints, not Big Tech flexing its muscles Boney M’s 1978 disco hit Rasputin and an Indian pop song called Maa Tujhe Salaam (Mother, I Salute You) have been revealed as the reason Twitter briefly suspended the accounts of two Indian politicians.…
|
 |
by Laura Dobberstein on (#5KXJ9)
Research agency also open-sources FETT hardware bug bounty platform and tools The USA’s Defense Advanced Research Projects Agency (DARPA) has announced it will fund development of a new type of “event-based” camera that only transmits information about pixels that have changed.…
|
 |
by Simon Sharwood on (#5KXF7)
Hikes numbers of known compromised customers and warns countermeasures will be needed before resuming usage Kaseya has said it’s been unable to find signs its code was maliciously modified, and offered its users a ray of hope with news that it is testing a patch for its on-prem software and is considering restoring its SaaS services on Tuesday, US Eastern Daylight Time (EDT).…
|
 |
by Simon Sharwood on (#5KXE7)
Current draft makes staff personally liable and Asia Internet Coalition says that could crimp innovation and hurt the economy The Asia Internet Coalition (AIC), a lobby group that numbers Apple, Facebook, Google, Yahoo! and SAP among its members, has written to Hong Kong’s Office of the Privacy Commissioner for Personal Data (PCPD) and outlined objections to the Special Administrative Region’s proposed anti-doxxing laws.…
|
 |
by Tim Richardson on (#5KXC1)
'Claims are up, capacity is down, and underwriting profitability is, at best, under pressure' The cost of insurance to protect businesses and organisations against the ever-increasing threat of cybercrimes has soared by a third in the last year, according to international insurance brokers Howden.…
|
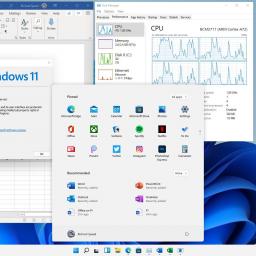 |
by Richard Speed on (#5KXAB)
When the Pi was loaded/ with native Windows 11 bling... wasn’t it quite Armful, a somewhat speedy thing The Register's adventures into the world of Pi-powered Windows 11 continued today with the installation of the ARM64 version of Microsoft's popular Office suite.…
|
 |
by Richard Speed on (#5KX8W)
'Foo' – not the noise of a passing car The world of Formula 1 racing was livened up over the weekend as the sport's official app sent out some unexpected notifications on the eve of the Austrian Grand Prix.…
|
 |
by Tim Richardson on (#5KX7E)
Hakuna matata The boss of Arm has moved to tackle prolonged concerns that the British chip designer's proposed $40bn buyout by Nvidia could damage competition and spell disaster for the UK's tech sector.…
|
 |
by Tim Anderson on (#5KX5G)
Torvalds reckons 'it might be mergeable for 5.14' The Rust for Linux project, sponsored by Google, has advanced with use of a beta Rust compiler (as opposed to a nightly build), testing ARM and RISC-V architecture support, new Rust abstractions, and more.…
|
 |
by Matthew Hughes on (#5KX2Y)
It's illegal The California Highway Patrol has issued a warning to motorists that, frankly, needn't be said. Don't whack a massive Starlink satellite dish to the hood of your car. It's a bit illegal.…
|
 |
by Laura Dobberstein on (#5KX0S)
Crew do some DIY, move a camera, you know, the usual … but in zero gravity The China Manned Space Agency (CMSA) has announced that two taikonauts successfully exited the Tianhe space station yesterday for China’s second ever spacewalk.…
|
 |
by Tim Richardson on (#5KX0T)
Contract worth £75m over seven years City of London Police is looking to crack down on cybercrime with the purchase of "next-generation IT services" in the hopes it will beef up the systems supporting Action Fraud and the National Fraud Intelligence Bureau (NFIB).…
|
 |
by David Gordon on (#5KWXW)
Learn how to swap tedium for transformation with this Regcast Webcast Does your tech strategy involve analytics, e-commerce, machine learning or even AI? Great, you’re probably going to need all of those in the future.…
|
 |
by Tim Richardson on (#5KWVP)
Mmm, musty One of London's tram stations – mothballed in 1952 to make way for diesel buses – is to be opened to the public.…
|
 |
by Richard Speed on (#5KWSF)
'Fork.' What did you think we meant? A few more litres of accelerant were poured onto Audacity critics' fire late last week as an update to the sound editor's privacy agreement seeped out to the consternation of users.…
|
 |
by Lindsay Clark on (#5KWSG)
Let's hope this time a shortage can be averted The UK government has awarded a £5m contract to build the second generation of its e-commerce portal to help health providers get hold of personal protection equipment (PPE) during the ongoing COVID-19 crisis.…
|
 |
by Paul Kunert on (#5KWPX)
Hired to boost channel sales and, erm, 'accelerate' that 'growth journey' Google Cloud has poached Adaire Fox-Martin, a veteran from the stuffy world of corporate database sales, to run its EMEA operations.…
|
 |
by Richard Speed on (#5KWNE)
Welcome to Madeira, autonomous region of Borkugal Bork!Bork!Bork! As the latest twist in the Windows 11 saga appears to have turned the blue in "Blue Screen of Death" to black, a glimpse into the international world of bork shows that a black background has always been the harbinger of a poorly computer.…
|
 |
by Lindsay Clark on (#5KWNF)
Foundry platform lacks transparency and accountability, sources tell El Reg Researchers at NHS England are being denied access to datasets on the Palantir platform which supports the COVID-19 data store, with no reason given, despite requests for greater transparency on the system.…
|
 |
by Rupert Goodwins on (#5KWKW)
Quit financial engineering and go back to your roots, IBM Column A fun evening's entertainment pre-COVID was to find a pub near a large corporation's IT HQ, look for the customers with the haunted, desperate eyes, and ask them gently how "the migration" was going. Didn't matter which company or what migration. They're hard. They go wrong.…
|
 |
by Scott Gilbertson on (#5KWJ6)
If Muse Group's stewardship takes a wrong turn, there's always the fork button* Updated The quality of software the FOSS community has created is nothing short of amazing.…
|
 |
by Richard Speed on (#5KWH3)
Enthusiasm and youth are once again no match for age and cunning Who, Me? With the use of personal email accounts seemingly never out of the political headlines, we present a cautionary tale of their career-shortening possibilities in another edition of Who, Me?…
|
 |
by Simon Sharwood on (#5KWG0)
Bakes in VPN, ad-blocker, even a crypto wallet, and claims it’s the only non-Chrome browser to harmonise with Google’s lightweight lappies Norwegian web developer Opera has created a version of its software optimised for Google’s ChromeOS.…
|
 |
by Laura Dobberstein on (#5KWER)
And so were two other app-makers that also happen to have listed in the USA lately Updated Chinese ride hailing app DiDi Chuxing was on Sunday removed from local app stores on on grounds that it did not comply with data protection laws. The ban came less than a week after the company’s US stock market debut.…
|
 |
by Simon Sharwood on (#5KWDD)
REvil ransomware rampages through managed services providers and perhaps 1,000 clients IT management software provider Kaseya has deferred an announcement about restoration of its SaaS services, after falling victim to a supply chain attack that has seen its products become a delivery mechanism for the REvil ransomware.…
|
 |
by Simon Sharwood on (#5KWAH)
Reg chats to developer whose joke that mere mention of a new prod would appear in job ads came true and spawned books, songs, forks, cryptocoin, and more A tweeted musing that merely mentioning a new AWS product would be enough to see it appear in job ads has come true — even though the product mentioned is made up.…
|
 |
by Iain Thomson on (#5KV67)
Plus: Cops seize 3D printers 'used to print guns', and more bits and bytes In brief In what's looking like a nasty supply-chain attack, IT systems management biz Kaseya was compromised by miscreants, which then used its VSA product to infect its own customers and then their customers with ransomware.…
|